
Refer to the exhibit. A Python API server has been deployed. Based on metrics and logs, increased load has been noticed. Which two approaches must be taken to optimize API usage on the server? (Choose two.)
Refer to the exhibits. Which data payload completes the CURL command to run the create port object API call In Cisco Firepower Threat Defense?
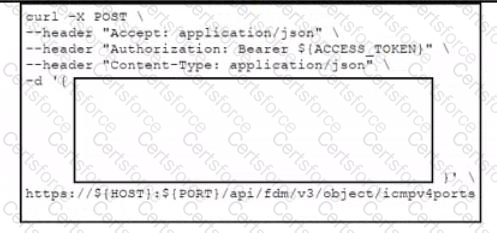
Refer to the exhibits. Which data payload completes the CURL command to run the create port object API call In Cisco Firepower Threat Defense?
A)

B)

C)

D)

A client is written that uses a REST API to interact with a server. Using HTTPS as the transport, an HTTP request is sent and received an HTTP response. The response contains the HTTP response status code: 503 Service Unavailable.
Which action is the appropriate response?
A developer is working in a branch to develop a new feature named ‘newfeat404880077’. A file named ‘devcoreg13642911.jpg’ has accidentally been staged. This needs to be removed so that the commit is performed and branches merged. Which git command must be used to unstage the file?
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances.
Which two actions can improve the design of the application to identify the faults? (Choose two.)
In the three-legged OAuth2 process, after the authorization server presents a form to the resource owner to grant access, what is the next step?
Which two gRPC modes of model-driven telemetry are supported on Cisco IOS XE Software? (Choose two.)
A Cisco Catalyst 9000 switch has guest shell enabled. Which Linux command installs a third-party application?
Cisco sensorBase gathers threat information from a variety of cisco products and services and performs analytics on threats. Which term describes this process?
Refer to the exhibit.
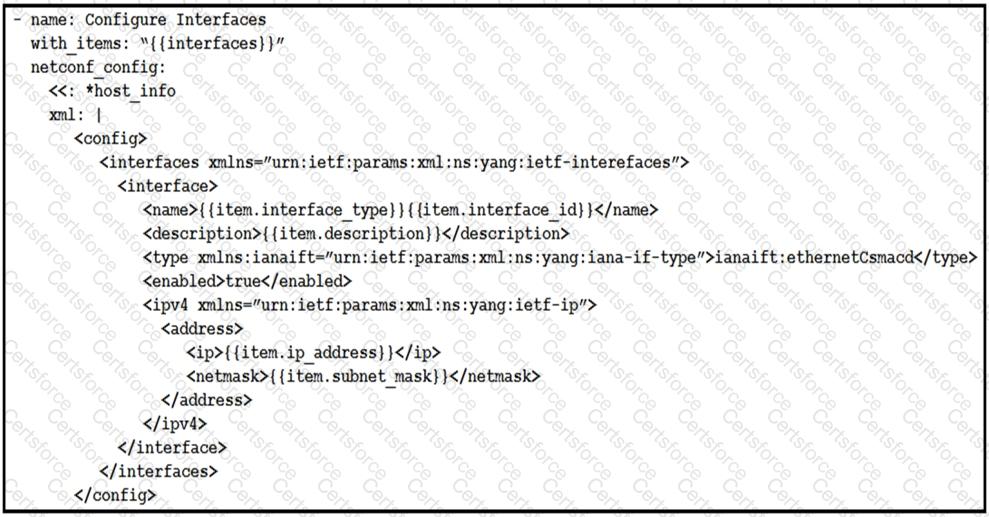
The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?