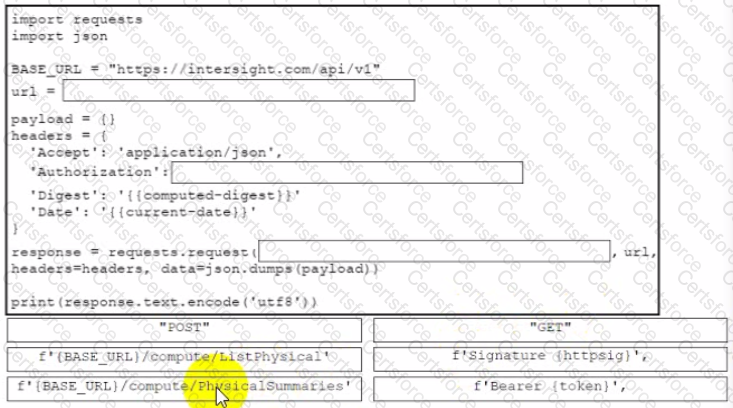
Drag and drop the code from the bottom onto the box where the code is missing to retrieve a summary of physical compute resources. The collected information about the compute resources will be presented in a dashboard to be developed for device monitoring purposes. Not all snippets are used.
A developer releases a new application for network automation of Cisco devices deployed in a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability- driven velopment lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
Which security approach should be used for developing a REST API?
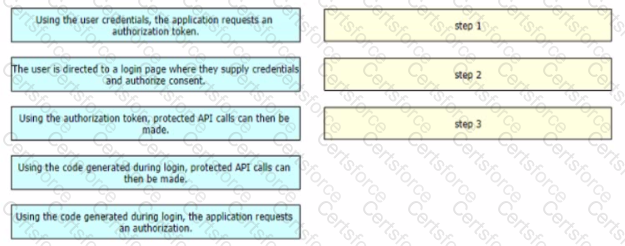
Drag and drop the steps from the left into the sequence on the fight to implement an OAuth2 three-legged authorization code flow grant type in an application Not all options are used.
Refer to the exhibit.
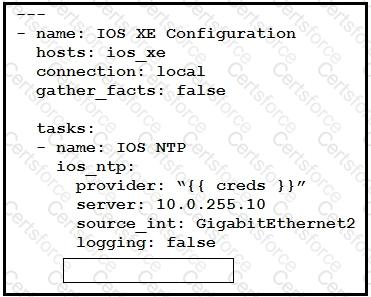
Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
A web application is being developed to provide online sales to a retailer. The customers will need to use their username and passwords to login into then profile and complete their order For this reason the application must store user passwords Which approach ensures that an attacker wifi need to crack the passwords one at a time?
Which RFC5988 (Web Linking) relation type is used in the Link header to control pagination in APIs?
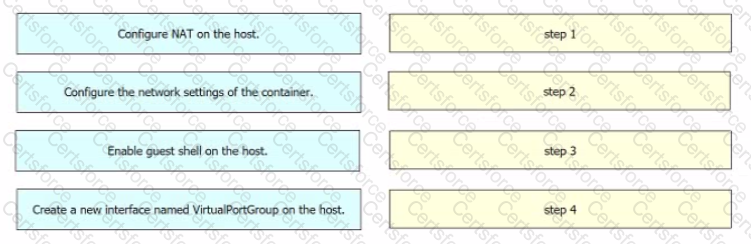
Drag and drop the steps from the left into the order on the right to ensure that an application requiring communication to the external network is hosted on a Cisco Catalyst 9000 switch.
Refer to the exhibit.
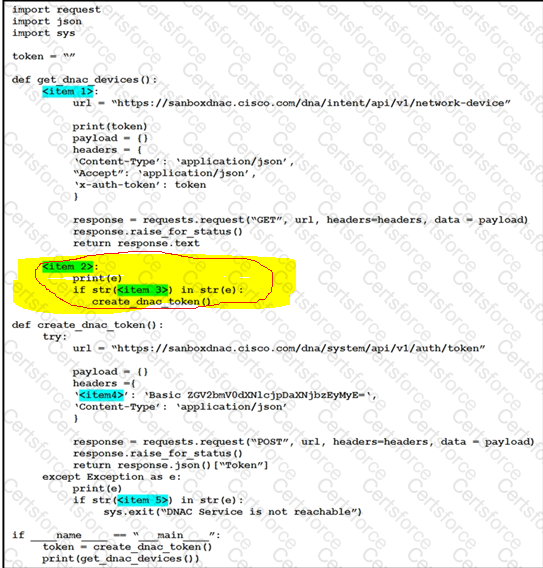
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
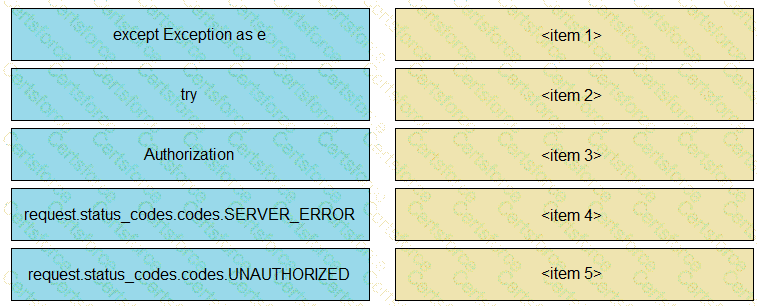
Refer to the exhibit.
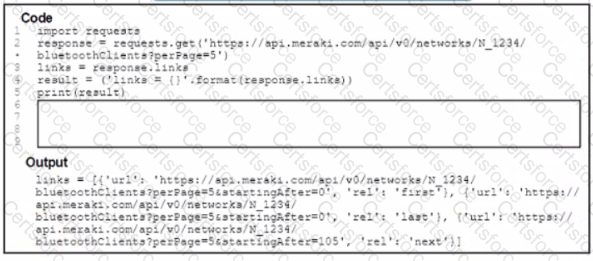
A Python script has these requirements
• Retrieve a list of Bluetooth clients seen by the access pants on a network.
• Print the content of the response
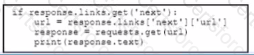
• Retrieve the next page only if it is available in the response headers
What must be added where the code is missing to get the remaining pages by using the next link from the link response header of the last request?
A)
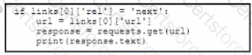
B)

C)
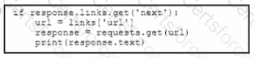
D)