Refer to the exhibit.
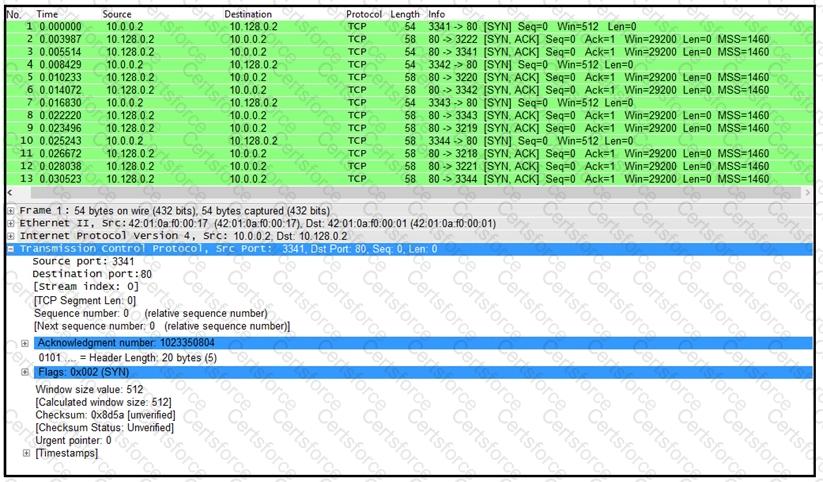
What is the threat in this Wireshark traffic capture?
Refer to the exhibit.

IDS is producing an increased amount of false positive events about brute force attempts on the organization’s mail server. How should the Snort rule be modified to improve performance?
Refer to the exhibit.
An engineer is performing static analysis of a file received and reported by a user. Which risk is indicated in this STIX?
An engineer received multiple reports from users trying to access a company website and instead of landing on the website, they are redirected to a malicious website that asks them to fill in sensitive personal data. Which type of attack is occurring?
Refer to the exhibit.
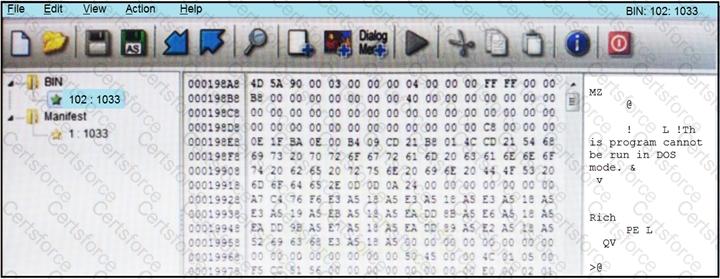
An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
Refer to the exhibit.
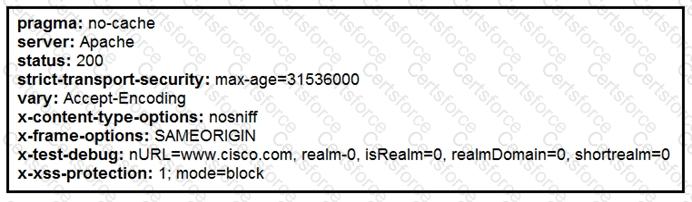
Where does it signify that a page will be stopped from loading when a scripting attack is detected?