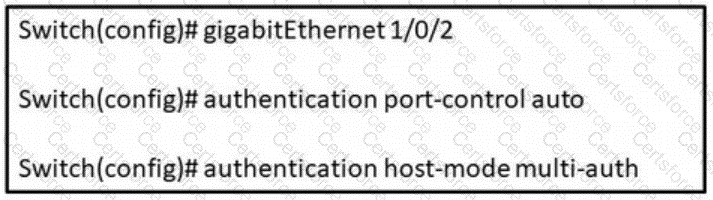
Refer to the exhibit. In which scenario does this switch configuration apply?
What is a characteristic of the UDP protocol?
A network engineer needs to ensure that the access credentials are not exposed during the 802.1x authentication among components. Which two protocols should complete this task?
An administrator connects an HP printer to a dot1x enable port, but the printer in not accessible Which feature must the administrator enable to access the printer?
What does a fully distributed Cisco ISE deployment include?
An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?
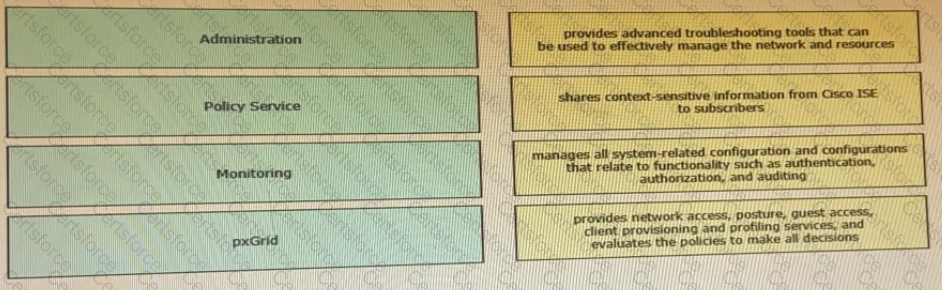
Drag the Cisco ISE node types from the left onto the appropriate purposes on the right.
What should be considered when configuring certificates for BYOD?
An engineer is implementing network access control using Cisco ISE and needs to separate the traffic based on the network device ID and use the IOS device sensor capability. Which probe must be used to accomplish this task?
An administrator needs to give the same level of access to the network devices when users are logging into them using TACACS+ However, the administrator must restrict certain commands based on one of three user roles that require different commands How is this accomplished without creating too many objects using Cisco ISE?