Which two actions occur when a Cisco ISE server device administrator logs in to a device? (Choose two)
Which Cisco ISE solution ensures endpoints have the latest version of antivirus updates installed before being allowed access to the corporate network?
Which two features should be used on Cisco ISE to enable the TACACS+ feature? (Choose two )
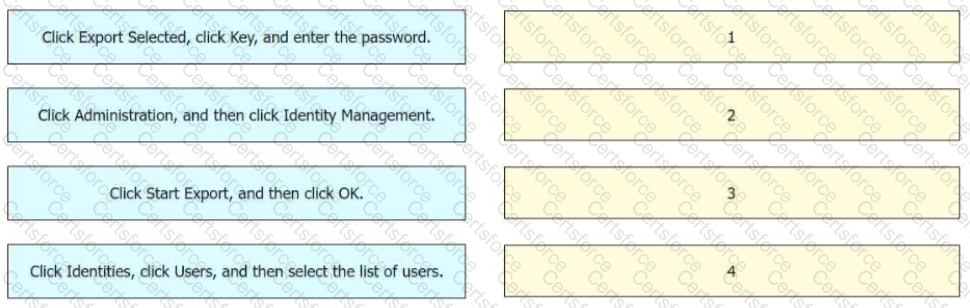
An engineer needs to export a file in CSV format, encrypted with the password C1$c0438563935, and contains users currently configured in Cisco ISE. Drag and drop the steps from the left into the sequence on the right to complete this task.
Which portal is used to customize the settings for a user to log in and download the compliance module?
When creating a policy within Cisco ISE for network access control, the administrator wants to allow different access restrictions based upon the wireless SSID to which the device is connecting. Which policy condition must be used in order to accomplish this?
A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task''
An administrator is manually adding a device to a Cisco ISE identity group to ensure that it is able to access the network when needed without authentication Upon testing, the administrator notices that the device never hits the correct authorization policy line using the condition EndPoints LogicalProfile EQUALS static_list Why is this occurring?
What are two differences between the RADIUS and TACACS+ protocols'? (Choose two.)
When setting up profiling in an environment using Cisco ISE for network access control, an organization must use non-proprietary protocols for collecting the information at layer 2. Which two probes will provide this information without forwarding SPAN packets to Cisco ISE? {Choose two.)