A company's security policy requires that all connections between sites be encrypted in a manner that does not
require maintenance of permanent tunnels. The sites are connected through a private MPLS-based service that
uses a dynamically changing key and spoke-to-spoke communication. Which type of transport encryption must
be used in this environment?
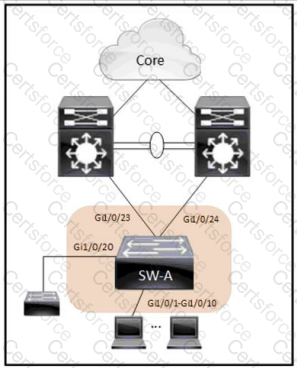
Refer to the exhibit. An architect reviews the low-level design of a company's enterprise network and advises optimizing the STP convergence time. Which functionality must be to Gi1/0/1-10 to follow the architect's recommendation?
An architect must develop a campus network solution that includes:
logically segmented and isolated networks
ability to communicate between network segments when required
support for overlapping IP addresses
widely available technologies to avoid purchasing specialized equipment
Which solution must the architect select?
An engineer is looking for a standards-driven YANG model to manage a multivendor network environment. Which model must the engineer choose?
Which common issue causes intermittent DMVPN tunnel flaps?
An engineer is designing a BGP network for a large customer. To permit efficient scaling, the BGP domain is split into clusters. Which peering solution should be used between the route reflectors in different clusters for the BGP routes to be propagated appropriately?
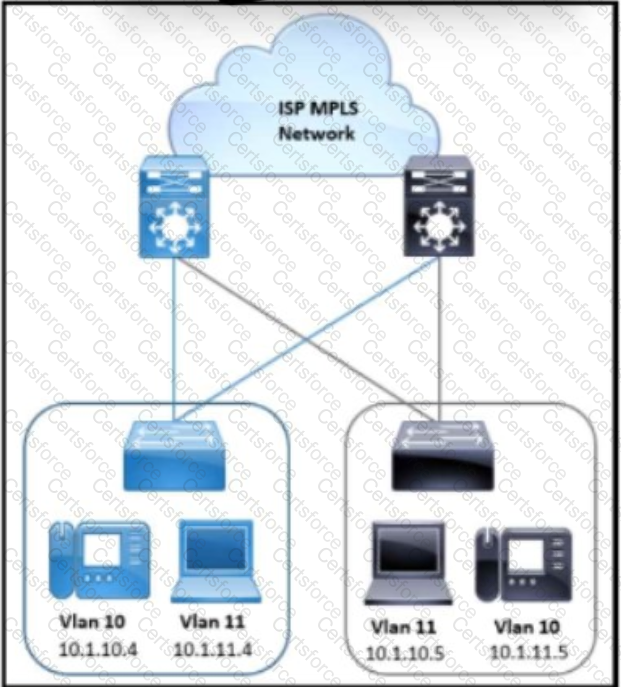
Refer to the exhibit. An architect must design a resilient gateway solution based on these requirements:
VLAN 10 and VLAN 11 support voice and video applications.
Link and node failures must have minimal impact on traffic.
Provide protection against false hello packets.
Support IPv6.
Which solution must the architect choose?
What is the main purpose of the Cisco SD-Access underlay design?
A company is planning to open two new branches and allocate the 2a01:c30:16:7009::3800/118 IPv6 network for the region. Each branch should have the capacity to accommodate maximum of 200 hosts. Which two networks should the company use? (Choose two.)
Which control plane protocol is responsible for ElD-to-RLOC mapping concerning SO-Access Architecture?