A threat hunter is asked to model how an attacker could abuse cloud identity misconfigurations to escalate privileges without exploiting software vulnerabilities. Which modeling approach BEST supports this analysis?
The SOC team receives an alert about a user sign-in from an unusual country. After investigating the SIEM logs, the team confirms the user never signed in from that country. The incident is reported to the IT administrator who resets the user's password. Which threat hunting phase was initially used?
A security analyst receives an alert that host A, which has an IP address of 192.168.5.39, has a new browser extension installed. During an investigation of the SIEM tool logs, the analyst discovers that host A made continuous TCP connections to an IP address of 1.25.241.8 via TCP port 80. The 1.25.241.8 IP address is categorized as a C2 server. Which action should the analyst take to mitigate similar connections in the future?
After completing a threat hunt that uncovered previously undetected credential abuse, the SOC wants to ensure long-term improvement in detection and response capabilities. Which action BEST represents the final and most critical phase of the threat hunting lifecycle?
A security operations team is transitioning from alert-driven investigations to a mature threat hunting program. The team wants to focus on detecting adversaries who intentionally evade signature-based tools and traditional SIEM alerts by using legitimate credentials and native system utilities. Which hunting focus best supports this objective?
A SOC repeatedly discovers similar attacker behaviors during separate hunts, indicating recurring detection gaps. What process change MOST effectively prevents rediscovery of the same threats?
Refer to the exhibit.
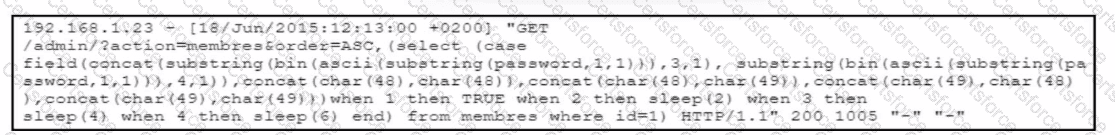
The cybersecurity team at a company detects an ongoing attack directed at the web server that hosts the company website. The team analyzes the logs of the web application firewall and discovers several HTTP requests encoded in Base64. The team decodes the payloads and retrieves the HTTP requests. What did the attackers use to exploit the server?
A SOC analyst is usingCisco Secure Network Analytics (Stealthwatch)to hunt for command-and-control (C2) activity across the enterprise. The analyst wants to identify stealthy C2 channels that intentionally avoid known malicious IP addresses and domains. Which Stealthwatch hunting approach BEST supports this objective?