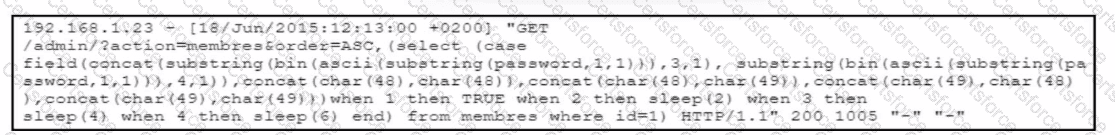
The correct answer is SQL injection. The decoded HTTP request shown in the exhibit contains multiple unmistakable indicators of a SQL injection attack, including the use of SQL keywords and functions such as SELECT, CASE, SUBSTRING, ASCII, BIN, and conditional SLEEP() statements. These elements are characteristic of time-based blind SQL injection, a technique attackers use to extract database information when direct query results are not visible.
From a professional cybersecurity perspective, the presence of expressions like:
SELECT (CASE WHEN … THEN SLEEP(x))
SUBSTRING(password,1,1)
ASCII() and binary conversions
indicates that the attacker is probing the backend database character by character and using response timing to infer whether conditions are true or false. This is a well-known exploitation method used when error messages or query output are suppressed by the application.
The use of Base64 encoding does not represent the attack itself but rather an obfuscation technique to evade basic web application firewall (WAF) signatures and logging visibility. Encoding payloads allows attackers to bypass simple pattern-matching defenses, but once decoded, the underlying SQL injection becomes evident.
Option A (Unicode encoding) is incorrect because Unicode is commonly used for evasion, not exploitation. Option C (directory traversal) typically involves sequences like ../ to access filesystem paths, which are not present. Option D (XSS) targets client-side script execution and would include JavaScript payloads rather than database-focused logic.
According to the MITRE ATT&CK framework, this activity maps to Initial Access – Exploit Public-Facing Application (T1190). SQL injection remains one of the most exploited vulnerabilities in public-facing applications due to poor input validation and insecure coding practices.
For threat hunters and defenders, this scenario reinforces the importance of deep payload inspection, decoding obfuscated requests, monitoring for anomalous database query behavior, and enforcing secure development practices such as parameterized queries and input sanitization. SQL injection continues to be a high-impact, real-world attack vector despite being well understood, making it a critical focus area in web application threat hunting.
Submit