What is a capability of Cisco Webex?
Which two commands download and execute an Apache web server container in Docker with a port binding 8080 in the container to 80 on the host? (Choose two.)
Refer to the exhibit.
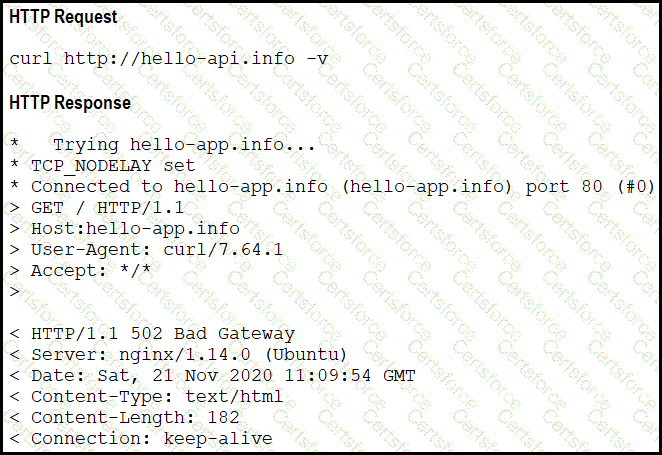
A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem?
In which way do webhooks notify a client about server or application changes by default?
An engineer must review and clean up a code repository. During the review, the engineer finds a file named config.json that contains API URLs, shared keys, and other application configurations. Which two methods, according to best practice, must be used to protect secrets? (Choose two.)
Which protocol is used for clock synchronization between network devices?
Which solution reduces costs from MPLS, improves application performance, and simplifies operations?
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
Which two details are captured from the subnet mask? (Choose two.)
Refer to the exhibit.
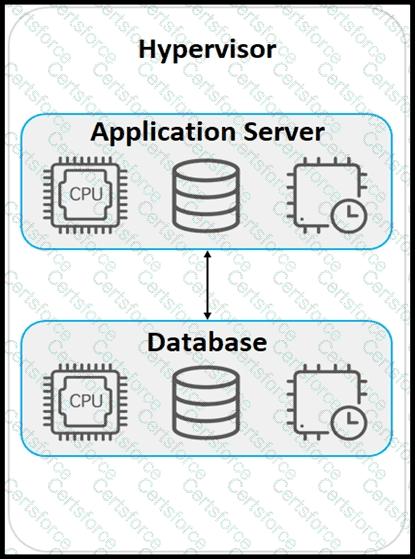
An application must be deployed on a server that has other applications installed. The server resources are to be allocated based on the deployment requirements. The OS for each application must be independent. Which type of deployment is used?