Which service is the minimum prerequisite needed if a customer wants to purchase ATP: Email?
Which two (2 non-Symantec method for restricting traffic are available to the Incident response team?
What does a Quarantine Firewall policy enable an ATP Administrator to do?
Which best practice does Symantec recommend with the Endpoint Detection and Response feature?
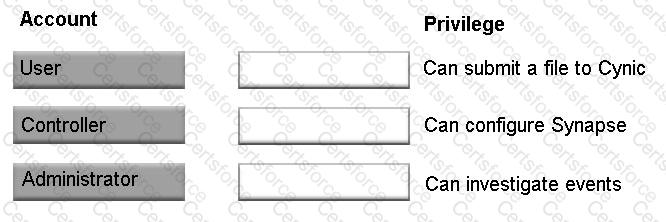
Which level of privilege corresponds to each ATP account type?
Match the correct account type to the corresponding privileges.
What is the earliest stage at which a SQL injection occurs during an Advanced Persistent Threat (APT) attack?
Which stage of an Advanced Persistent Threat (APT) attack do attackers break into an organization’s network
to deliver targeted malware?
In which two locations should an Incident Responder gather data for an After Actions Report in ATP? (Choose
two.)
How does an attacker use a zero-day vulnerability during the Incursion phase?
Which section of the ATP console should an ATP Administrator use to evaluate prioritized threats within the environment?