What does "network delay" mean within PacketShaper?
A university warns to provide each student a minimum of 30 Kbps and a maximum ofISO Kbps to be used in any way. Which control mechanism does Symantec recommend to ensure this capacity?
Which statement accurately describes rate policies and priority policies?
Which option does Symantec recommend to
What is required on the network to allow classification of traffic flow by a specific user?
Which two (2) actions are most appropriate for controlling prohibited, unsanctioned traffic flows such as music downloads? (Select two)
Refer to the exhibit.
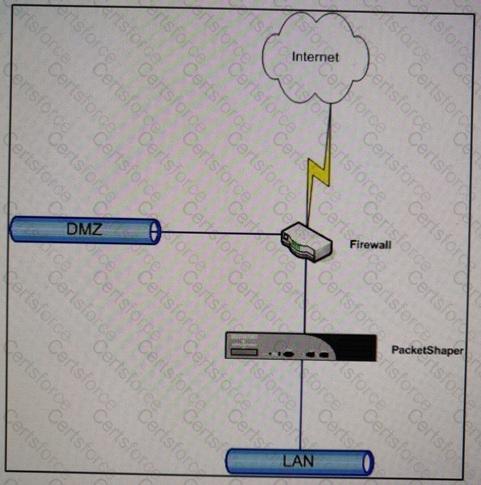
Which task must the administrator perform to make sure that traffic between (he IAN and DMZ is treated as pass-through PacketShaper installed as shown?
Refer to the exhibit.
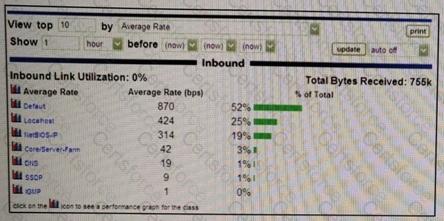
Which PacketShaper feature is shown here?
Which feature can be used to modify the amount of bandwidth available to an application based on the time of day?
When would the traffic class Inbound/HTTP inherit its policy from another class?