A playbook loop that interacts with Active Directory for user details (yielding extensive data) is altered to extract newly acquired indicators of compromise (IOCs). This change results in two critical issues:
• Rate limits being hit on integrated reputation services
• Incidents associated with hundreds of indicators
Given the settings below, what would prevent the issues in this use case?
Incident Type: AD-Analysis –
Extract Indicators on Incident Creation: Use System Default (None)
Extract Indicators on Field Change: Inline
Task 1: ad-get-user –
Mark results as note: False –
Indicator Extract Mode: Inline –
Quiet Mode: False –
Task 2: ad-disable-account –
Mark results as note: True –
Indicator Extract Mode: None –
Quiet Mode: True –
Task 3: servicenow-update-ticket –
Mark results as note: False –
Indicator Extract Mode: Use System Default
Quiet Mode: False
What is the primary effect on a new file hash when it is added to the indicator exclusion list?.
What happens if both a Classifier and Incident Type are configured in an integration instance's settings?
A playbook task generates a report as HTML in the context data.
An engineer creates a custom indicator field of type "HTML" and adds the field to a section in a custom indicator layout. How can the engineer populate the HTML field in the indicator layout?
What is the function of timer SLA fields in Cortex XSOAR?
Which field type provides an interactive and editable display of table-based data?
Which component can be part of a load balancing group?
Which XSOAR architecture would be recommended for Managed Security Service Providers (MSSP)?
An organization has recently acquired another company as its subsidiary. The subsidiary has its infrastructure on AWS cloud as illustrated in the image below:
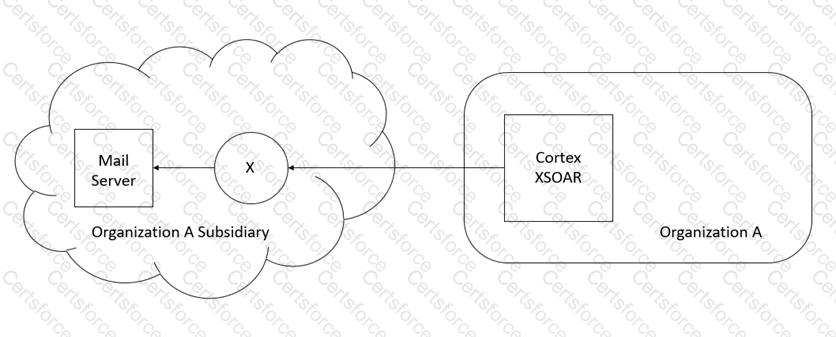
The organization wants to use the mail server location on the subsidiary's cloud to send emails. Without acquiring additional licenses, which XSOAR component can fulfill the requirement?
Where does the mapping of user groups to SAML groups take place?.