Based on the Malware profile image below, what happens when a new custom-developed application attempts to execute on an endpoint?

It will immediately execute
It will not execute
It will execute after one hour
It will execute after the second attempt
Since no image was provided, I assume the Malware profile is configured with default Cortex XDR settings, which typically enforce strict malware prevention for unknown or untrusted executables. In Cortex XDR, theMalware profilewithin the security policy determines how executables are handled on endpoints. For anew custom-developed application(an unknown executable not previously analyzed or allow-listed), the default behavior is toblock executionuntil the file is analyzed byWildFire(Palo Alto Networks’ cloud-based threat analysis service) or explicitly allowed via policy.
Correct Answer Analysis (B):By default, Cortex XDR’s Malware profile is configured toblockunknown executables, including new custom-developed applications, to prevent potential threats. When the application attempts ilustrator execute, the Cortex XDR agent intercepts it, sends it to WildFire for analysis (if not excluded), and blocks execution until a verdict is received. If the application is not on an allow list or excluded, itwill not executeimmediately, aligning with option B.
Why not the other options?
A. It will immediately execute: This would only occur if the application is on an allow list or if the Malware profile is configured to allow unknown executables, which is not typical for default settings.
C. It will execute after one hour: There is no default setting in Cortex XDR that delays execution for one hour. Execution depends on the WildFire verdict or policy configuration, not a fixed time delay.
D. It will execute after the second attempt: Cortex XDR does not have a mechanism that allows execution after a second attempt. Execution is either blocked or allowed based on policy and analysis results.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains Malware profile behavior: “By default, unknown executables are blocked until a WildFire verdict is received, ensuring protection against new or custom-developed applications” (paraphrased from the Malware Profile Configuration section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers Malware profiles, stating that “default settings block unknown executables to prevent potential threats until analyzed” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “Cortex XDR agent configuration” as a key exam topic, encompassing Malware profile settings.
Multiple remote desktop users complain of in-house applications no longer working. The team uses macOS with Cortex XDR agents version 8.7.0, and the applications were previously allowed by disable prevention rules attached to the Exceptions Profile "Engineer-Mac." Based on the images below, what is a reason for this behavior?
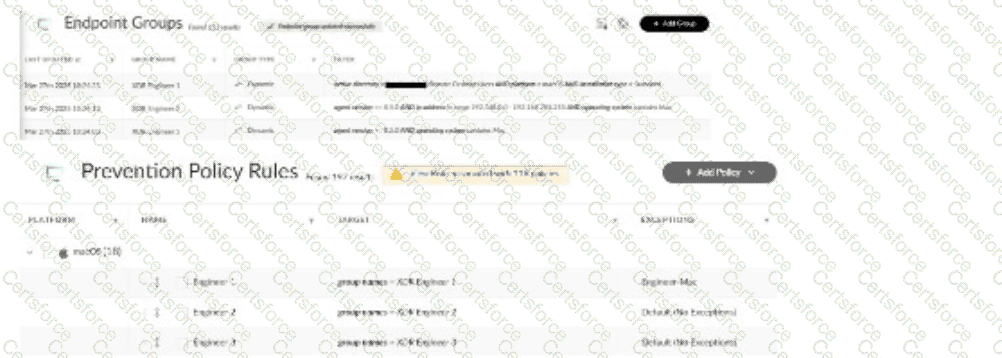
Endpoint IP address changed from 192.168.0.0 range to 192.168.100.0 range
The Cloud Identity Engine is disconnected or removed
XDR agent version was downgraded from 8.7.0 to 8.4.0
Installation type changed from VDI to Kubernetes
The scenario involves macOS users with Cortex XDR agents (version 8.7.0) who can no longer run in-house applications that were previously allowed via disable prevention rules in the"Engineer-Mac" Exceptions Profile. This profile is applied to an endpoint group (e.g., "Mac-Engineers"). Theissue likely stems from a change in the endpoint group’s configuration or the endpoints’ attributes, affecting policy application.
Correct Answer Analysis (A):The reason for the behavior is that theendpoint IP address changed from 192.168.0.0 range to 192.168.100.0 range. In Cortex XDR, endpoint groups can be defined using dynamic criteria, such as IP address ranges, to apply specific policies like the "Engineer-Mac" Exceptions Profile. If the group "Mac-Engineers" was defined to include endpoints in the 192.168.0.0 range, and the remote desktop users’ IP addresses changed to the 192.168.100.0 range (e.g., due to a network change or VPN reconfiguration), these endpoints would no longer belong to the "Mac-Engineers" group. As a result, the "Engineer-Mac" Exceptions Profile, which allowed the in-house applications, would no longer apply, causing the applications to be blocked by default prevention rules.
Why not the other options?
B. The Cloud Identity Engine is disconnected or removed: The Cloud Identity Engine provides user and group data for identity-based policies, but it is not directly related to Exceptions Profiles or application execution rules. Its disconnection would not affect the application of the "Engineer-Mac" profile.
C. XDR agent version was downgraded from 8.7.0 to 8.4.0: The question states the users are using version 8.7.0, and there’s no indication of a downgrade. Even if a downgrade occurred, it’s unlikely to affect the application of an Exceptions Profile unless specific features were removed, which is not indicated.
D. Installation type changed from VDI to Kubernetes: The installation type (e.g., VDI for virtual desktops or Kubernetes for containerized environments) is unrelated to macOS endpoints running remote desktop sessions. This change would not impact the application of the Exceptions Profile.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains endpoint group policies: “Dynamic endpoint groups based on IP address ranges apply policies like Exceptions Profiles; if an endpoint’s IP changes to a different range, it may no longer belong to the group, affecting policy enforcement” (paraphrased from the Endpoint Management section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers policy application, stating that “changes in IP address ranges can cause endpoints to fall out of a group, leading to unexpected policy behavior like blocking previously allowed applications” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “Cortex XDR agent configuration” as a key exam topic, encompassing endpoint group and policy management.
An XDR engineer is configuring an automation playbook to respond to high-severity malware alerts by automatically isolating the affected endpoint and notifying the security team via email. The playbook should only trigger for alerts generated by the Cortex XDR analytics engine, not custom BIOCs. Which two conditions should the engineer include in the playbook trigger to meet these requirements? (Choose two.)
Alert severity is High
Alert source is Cortex XDR Analytics
Alert category is Malware
Alert status is New
In Cortex XDR,automation playbooks(also referred to as response actions or automation rules) allow engineers to define automated responses to specific alerts based on trigger conditions. The playbook in this scenario needs to isolate endpoints and send email notifications for high-severity malware alerts generated by the Cortex XDR analytics engine, excluding custom BIOC alerts. To achieve this, the engineer must configure the playbook trigger with conditions that match the alert’s severity, category, and source.
Correct Answer Analysis (A, C):
A. Alert severity is High: The playbook should only trigger for high-severity alerts, as specified in the requirement. Setting the conditionAlert severity is Highensures that only alerts with a severity level of "High" activate the playbook, aligning with the engineer’s goal.
C. Alert category is Malware: The playbook targets malware alerts specifically. The conditionAlert category is Malwareensures that the playbook only responds to alerts categorized as malware, excluding other types of alerts (e.g., lateral movement, exploit).
Why not the other options?
B. Alert source is Cortex XDR Analytics: While this condition would ensure the playbook triggers only for alerts from the Cortex XDR analytics engine (and not custom BIOCs), the requirement to exclude BIOCs is already implicitly met because BIOC alerts are typically categorized differently (e.g., as custom alerts or specific BIOC categories). The alert category (Malware) and severity (High) conditions are sufficient to target analytics-driven malware alerts, and adding the source condition is not strictly necessary for the stated requirements. However, if the engineer wanted to be more explicit, this condition could be considered, but the question asks for the two most critical conditions, which are severity and category.
D. Alert status is New: The alert status (e.g., New, In Progress, Resolved) determines the investigation stage of the alert, but the requirement does not specify that the playbook should only trigger for new alerts. Alerts with a status of "InProgress" could still be high-severity malware alerts requiring isolation, so this condition is not necessary.
Additional Note on Alert Source: The requirement to exclude custom BIOCs and focus on Cortex XDR analytics alerts is addressed by theAlert category is Malwarecondition, as analytics-driven malware alerts (e.g., from WildFire or behavioral analytics) are categorized as "Malware," while BIOC alerts are often tagged differently (e.g., as custom rules). If the question emphasized the need to explicitly filter by source, option B would be relevant, but the primary conditions for the playbook are severity and category.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains automation playbook triggers: “Playbook triggers can be configured with conditions such as alert severity (e.g., High) and alert category (e.g., Malware) to automate responses like endpoint isolation and email notifications” (paraphrased from the Automation Rules section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers playbook creation, stating that “conditions like alert severity and category ensure playbooks target specific alert types, such as high-severity malware alerts from analytics” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “playbook creation and automation” as a key exam topic, encompassing trigger condition configuration.
During deployment of Cortex XDR for Linux Agents, the security engineering team is asked to implement memory monitoring for agent health monitoring. Which agent service should be monitored to fulfill this request?
dypdng
clad
pyxd
pmd
Cortex XDR agents on Linux consist of several services that handle different aspects of agent functionality, such as event collection, policy enforcement, and health monitoring.Memory monitoringfor agent health involves tracking the memory usage of the agent’s core processes to ensure they are operating within acceptable limits, which is critical for maintaining agent stability and performance. Thepmd(Process Monitoring Daemon) service is responsible for monitoring the agent’s health, including memory usage, on Linux systems.
Correct Answer Analysis (D):Thepmdservice should be monitored to fulfill the request for memory monitoring. The Process Monitoring Daemon tracks the Cortex XDR agent’s resource usage, including memory consumption, and reports health metrics to the console. Monitoring this service ensures the agent remains healthy and can detect issues like memory leaks or excessive resource usage.
Why not the other options?
A. dypdng: This is not a valid Cortex XDR service on Linux. It appears to be a typo or a misnamed service.
B. clad: The clad service (Cortex Linux Agent Daemon) is responsible for core agent operations, such as communication with the Cortex XDR tenant, but it is not specifically focused on memory monitoring for health purposes.
C. pyxd: The pyxd service handles Python-based components of the agent, such asscript execution for certain detections, but it is not responsible for memory monitoring or agent health.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains Linux agent services: “The pmd (Process Monitoring Daemon) service on Linux monitors agent health, including memory usage, to ensure stable operation” (paraphrased from the Linux Agent Deployment section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers Linux agent setup, stating that “pmd is the service to monitor for agent health, including memory usage, on Linux systems” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “planning and installation” as a key exam topic, encompassing Linux agent deployment and monitoring.
What is a benefit of ingesting and forwarding Palo Alto Networks NGFW logs to Cortex XDR?
Sending endpoint logs to the NGFW for analysis
Blocking network traffic based on Cortex XDR detections
Enabling additional analysis through enhanced application logging
Automated downloading of malware signatures from the NGFW
IntegratingPalo Alto Networks Next-Generation Firewalls (NGFWs)with Cortex XDR by ingesting and forwarding NGFW logs allows for enhanced visibility and correlation across network and endpoint data. NGFW logs contain detailed information about network traffic, applications, and threats, which Cortex XDR can use to improve its detection and analysis capabilities.
Correct Answer Analysis (C):Enabling additional analysis through enhanced application loggingis a key benefit. NGFW logs include application-layer data (e.g., App-ID, user activity, URL filtering), which Cortex XDR can ingest to perform deeper analysis, such as correlating network events with endpoint activities. This enhanced logging enables better incident investigation, threat detection, and behavioral analytics by providing a more comprehensive view of the environment.
Why not the other options?
A. Sending endpoint logs to the NGFW for analysis: The integration is about forwarding NGFW logs to Cortex XDR, not the other way around. Endpoint logs are not sent to the NGFW for analysis in this context.
B. Blocking network traffic based on Cortex XDR detections: While Cortex XDR can share threat intelligence with NGFWs to block traffic (via mechanisms like External Dynamic Lists), this is not the primary benefit of ingesting NGFW logs into Cortex XDR. The focus here is on analysis, not blocking.
D. Automated downloading of malware signatures from the NGFW: NGFWs do not provide malware signatures to Cortex XDR. Malware signatures are typically sourced from WildFire (Palo Alto Networks’ cloud-based threat analysis service), not directly from NGFW logs.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains NGFW integration: “Ingesting Palo Alto Networks NGFW logs into Cortex XDR enables additional analysis through enhanced application logging, improving visibility and correlation across network and endpoint data” (paraphrased from the Data Ingestion section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers NGFW log integration, stating that “forwarding NGFW logs to Cortex XDR enhancesapplication-layer analysis for better threat detection” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “data ingestion and integration” as a key exam topic, encompassing NGFW log integration.
