A network engineer troubleshoots a VPN Phase 2 mismatch and decides that PFS (Perfect Forward Secrecy) needs to be enabled. What action should the engineer take?
What are three prerequisites to enable Credential Phishing Prevention over SSL? (Choose three
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment
Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
When a new firewall joins a high availability (HA) cluster, the cluster members will synchronize all existing sessions over which HA port?
Which feature can provide NGFWs with User-ID mapping information?
An administrator has purchased WildFire subscriptions for 90 firewalls globally.
What should the administrator consider with regards to the WildFire infra-structure?
An administrator has been asked to configure active/passive HA for a pair of Palo Alto Networks NGFWs. The administrator assigns priority 100 to the active firewall.
Which priority is correct for the passive firewall?
What happens when the log forwarding built-in action with tagging is used?
A company wants to implement threat prevention to take action without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
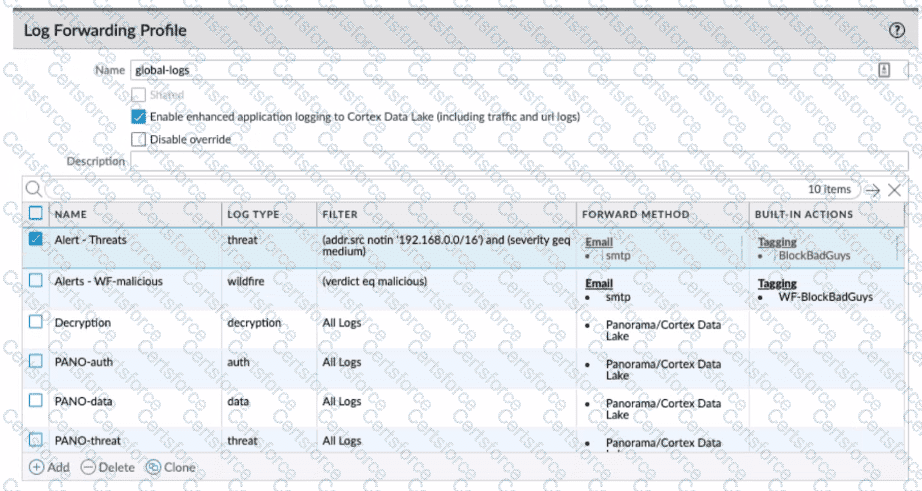
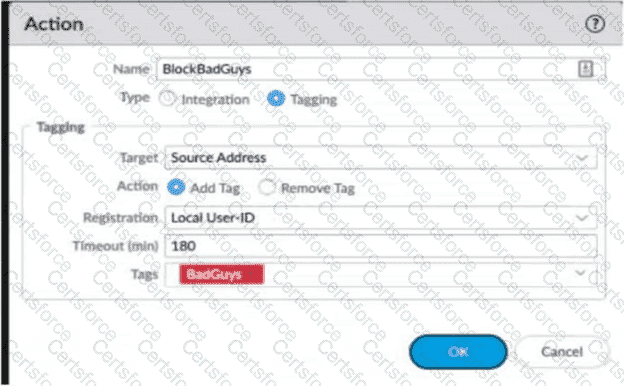
Review the images. A firewall policy that permits web traffic includes the global-logs policy is depicted
What is the result of traffic that matches the "Alert - Threats" Profile Match List?