You are auditing the work of a co-worker and need to verify that they have matched the Palo Alto Networks Best Practices for Anti-Spyware Profiles.
For which three severity levels should single-packet captures be enabled to meet the Best Practice standard? (Choose three.)
A firewall administrator has configured User-ID and deployed GlobalProtect, but there is no User-ID showing in the traffic logs.
How can the administrator ensure that User-IDs are populated in the traffic logs?
An engineer needs to configure a standardized template for all Panorama-managed firewalls. These settings will be configured on a template named "Global" and will be included in all template stacks.
Which three settings can be configured in this template? (Choose three.)
A customer requires that virtual systems with separate virtual routers can communicate with one another within a Palo Alto Networks firewall. In addition to confirming Security policies, which three configurations will accomplish this goal? (Choose three)
A network security administrator has been tasked with deploying User-ID in their organization.
What are three valid methods of collecting User-ID information in a network? (Choose three.)
How can a firewall be set up to automatically block users as soon as they are found to exhibit malicious behavior via a threat log?
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
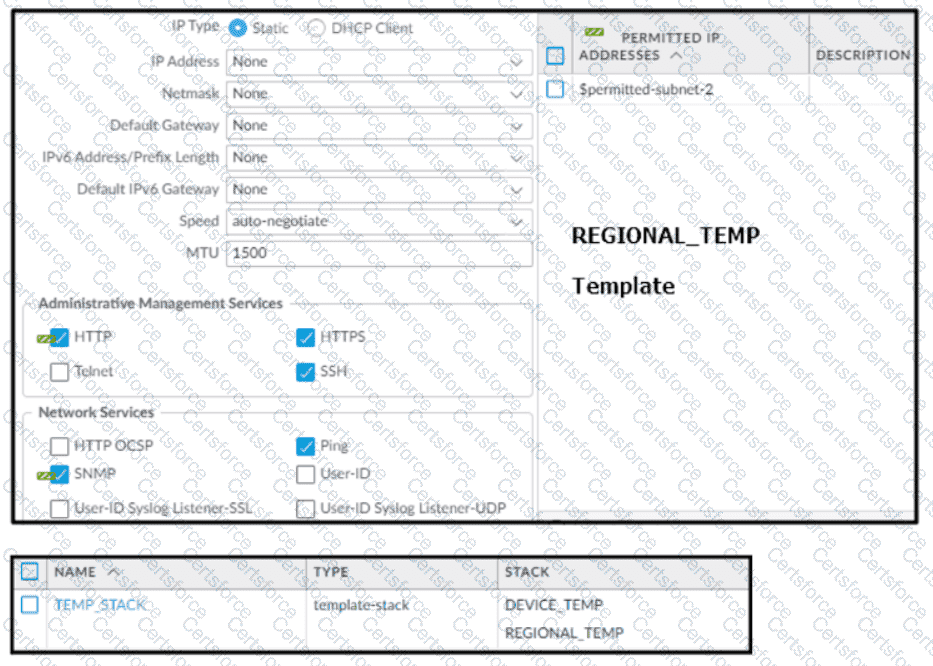
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
Panorama is being used to upgrade the PAN-OS version on a pair of firewalls in an active/passive high availability (HA) configuration. The Palo Alto Networks best practice upgrade steps have been completed in Panorama (Panorama upgraded, backups made, content updates, and disabling "Preemptive" pushed), and the firewalls are ready for upgrade. What is the next best step to minimize downtime and ensure a smooth transition?
Which statement accurately describes how web proxy is run on a firewall with multiple virtual systems?