Which two statements describe the functions of Session Border Controllers? (Choose two.)
After configuring Header Manipulation Rules (HMRs) for topology hiding, your subsequent testing shows that the manipulation is not taking effect.
Identify two causes for this (Choose two.)
You are troubleshooting a SIP routing issue and you have access to the SIP call flow processed by the Session Border Controller.
Which two steps are valid for troubleshooting this type of issues? (Choose two.)
What is used by the standby Session Border Controller to send ARP requests via the media interface in a High Availability (HA) architecture?
Your customer would like to allow call attempts only from User Agents (UAs) who have previously registered through the Session Border Controller or who are configured as session agents.
How would you accomplish this?
You are configuring access rules in a Session Border Controller Peering architecture.
Which configuration step is required to allow access from any User Agent (UA)?
What is the effect of executing the save-config command in superuser mode?
Which three statements are true about the bootloader? (Choose three.)
Examine the output below from the show sipd invite command:
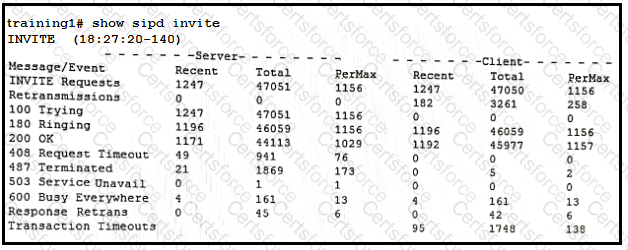
How many 600 Busy Everywhere messages sent by the Session Border Controller in the last 140 seconds did not originate from a downstream device?
Which three options are valid ways to apply Header Manipulation Rules (HMRs) to your existing configuration?