Your customer has deployed the Netskope client to secure their Web traffic. Recently, they have enabled Cloud Firewall (CFW) to secure all outbound traffic for their endpoints. Through a recent acquisition, they must secure all outbound traffic at several remote offices where they have access to the local security stack (routers and firewalls). They cannot install the Netskope client.
Review the exhibit.
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
You are given an MD5 hash of a file suspected to be malware by your security incident response team. They ask you to offer insight into who has encountered this file and from where was the threat initiated. In which two Skope IT events tables would you search to find the answers to these questions? (Choose two.)
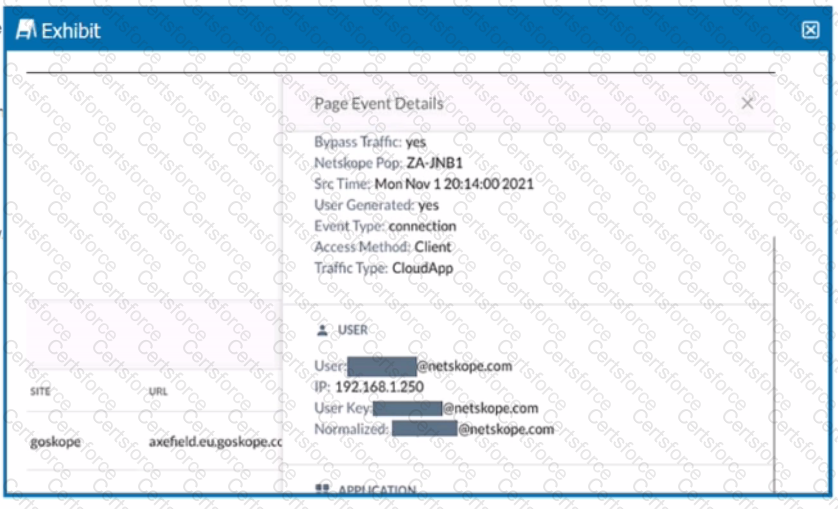
Review the exhibit.
Referring to the exhibit, which three statements are correct? (Choose three.)
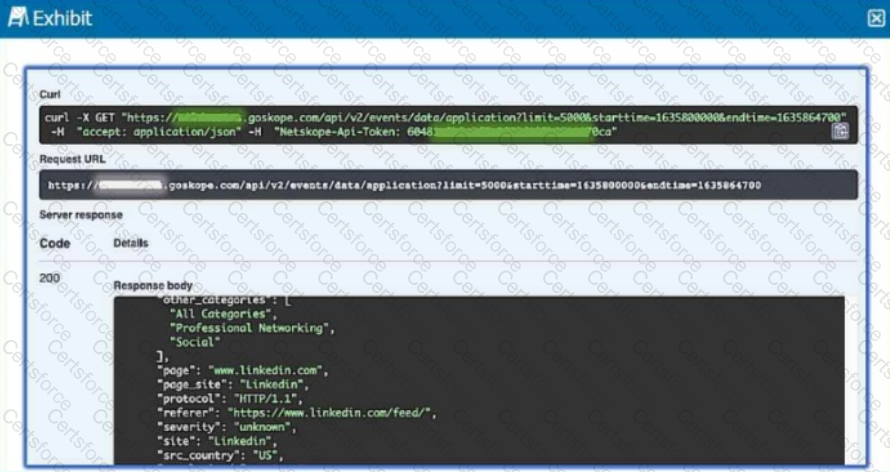
Review the exhibit.
add log-upload syslogng parserconfig set log-upload syslogng parserconfig 0
logsource <log-source>
You are asked to deploy a virtual appliance OPLP to accept syslog messages directly from the enterprise Palo Alto Networks firewall. You believe that you have configured the OPLP to accept the firewall logs, yet they are not appearing in Risk Insights. Referring to the exhibit, which parser name would be required to complete the new configuration?
A city uses many types of forms, including permit applications. These forms contain personal and financial information of citizens. Remote employees download these forms and work directly with the citizens to complete them. The city wants to be able to identify and monitor the specific forms and block the employees from downloading completed forms.
Which feature would you use to accomplish this task?
Your company wants to know if there has been any unusual user activity. In the UI, you go to Skope IT -> Alerts.
Which two types of alerts would you filter to find this information? (Choose two.)
You want to provision users and groups to a Netskope tenant. You have Microsoft Active Directory servers hosted in two different forests. Which statement is true about this scenario?
Your IT organization is migrating its user directory services from Microsoft Active Directory to a cloud-based Identity Provider (IdP) solution, Azure AD. You are asked to adapt the Netskope user provisioning process to work with this new cloud-based IdP.
You are deploying a Netskope client in your corporate office network. You are aware of firewall or proxy rules that need to be modified to allow traffic.
Which two statements are true in this scenario? (Choose two.)