In the Tenant III, which two methods would an administrator use to update a File Profile with malicious file hashes? (Choose two)
You want to block access to sites that use self-signed certificates. Which statement is true in this scenario?
What information is displayed in an application's Cloud Confidence Index (CCI) page? (Choose two.)
Exhibit
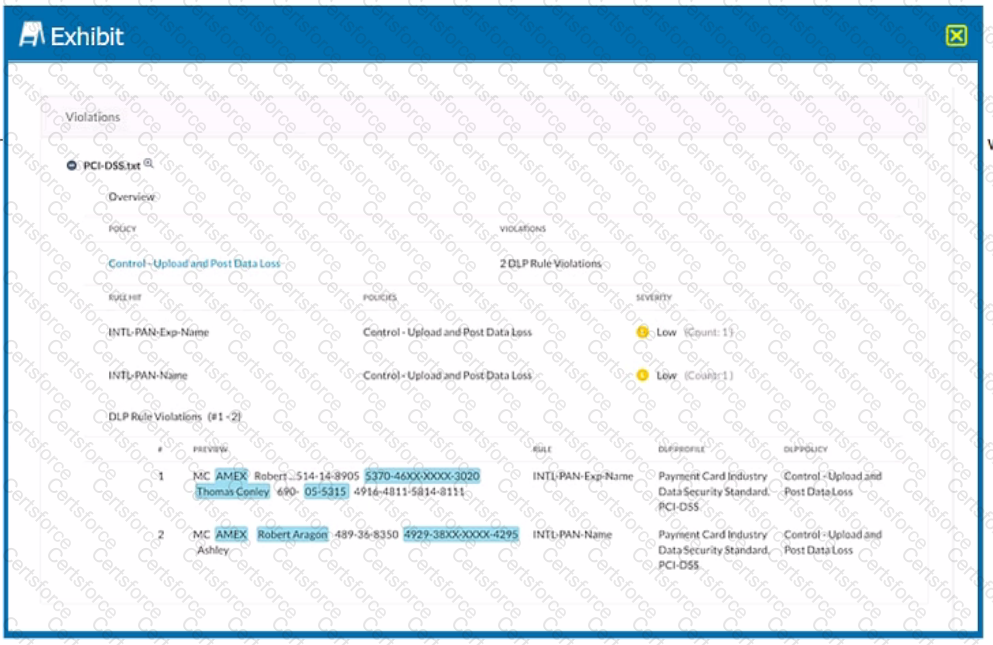
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
Your company started deploying the latest version of the Netskope Client and you want to track the progress and device count using Netskope.
Which two statements are correct in this scenario? (Choose two.)
As an administrator, you need to configure the Netskope Admin UI to be accessible by specific IP addresses and to display a custom message after the admin users have been authenticated.
Which two statements are correct in this scenario? (Choose two.)
Which two cloud security and infrastructure enablement technologies does Secure Access Service Edge (SASE) combine into its unified platform? (Choose two.)
You are required to present a view of all upload activities completed by users tunneled from the Los Angeles office to cloud storage applications.
Which two basic filters would you use on the SkopeIT Applications page to satisfy this requirement? (Choose two.)