You have an Azure subscription that uses Microsoft Defender for Cloud.
You need to configure Defender for Cloud to mitigate the following risks:
• Vulnerabilities within the application source code
• Exploitation toolkits in declarative templates
• Operations from malicious IP addresses
• Exposed secrets
Which two Defender for Cloud services should you use? Each correct answer presents part of the solution.
NOTE: Each correct answer is worth one point.
You have an Azure subscription that contains the users shown in the following table.
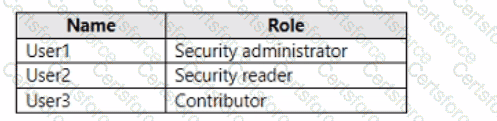
You need to delegate the following tasks:
• Enable Microsoft Defender for Servers on virtual machines.
• Review security recommendations and enable server vulnerability scans.
The solution must use the principle of least privilege.
Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR.
The security team at your company detects command and control (C2) agent traffic on the network. Agents communicate once every 50 hours.
You need to create a Microsoft Defender XDR custom detection rule that will identify compromised devices and establish a pattern of communication. The solution must meet the following requirements:
• Identify all the devices that have communicated during the past 14 days.
• Minimize how long it takes to identify the devices.
To what should you set the detection frequency for the rule?
Your company uses Azure Sentinel.
A new security analyst reports that she cannot assign and dismiss incidents in Azure Sentinel. You need to resolve the issue for the analyst. The solution must use the principle of least privilege. Which role should you assign to the analyst?
A company uses Azure Sentinel.
You need to create an automated threat response.
What should you use?
You have a Microsoft 365 E5 subscription that uses Microsoft Purview and contains a user named User1.
User1 shares a Microsoft Power Bi report file from the Microsoft OneDrive folder of your company to an external user by using Microsoft Teams.
You need to identity which Power BI report file was shared.
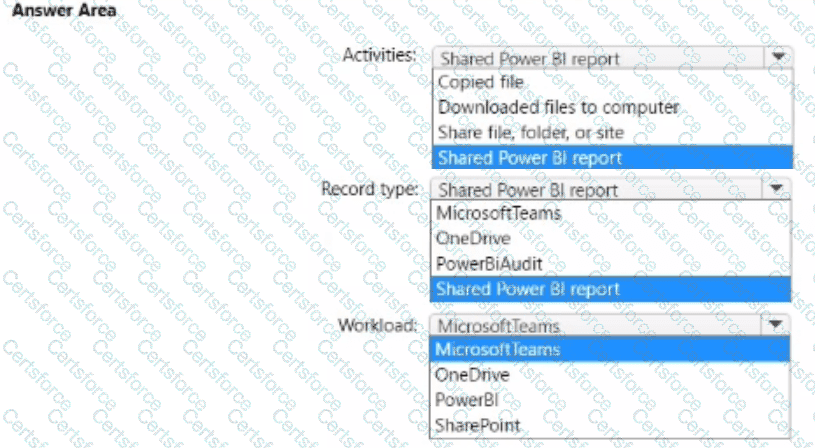
How should you configure the search? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and contains a Windows device named Device1.
You detect malicious activity on Device1.
You initiate a live response session on Device1.
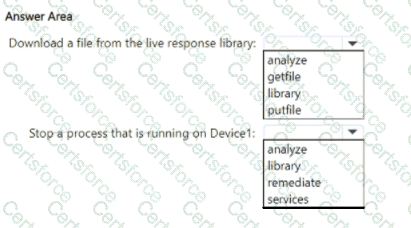
You need to perform the following actions:
• Download a file from the live response library.
• Stop a process that is running on Device1.
Which live response command should you run for each action? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft Sentinel workspace.
A Microsoft Sentinel incident is generated as shown in the following exhibit.
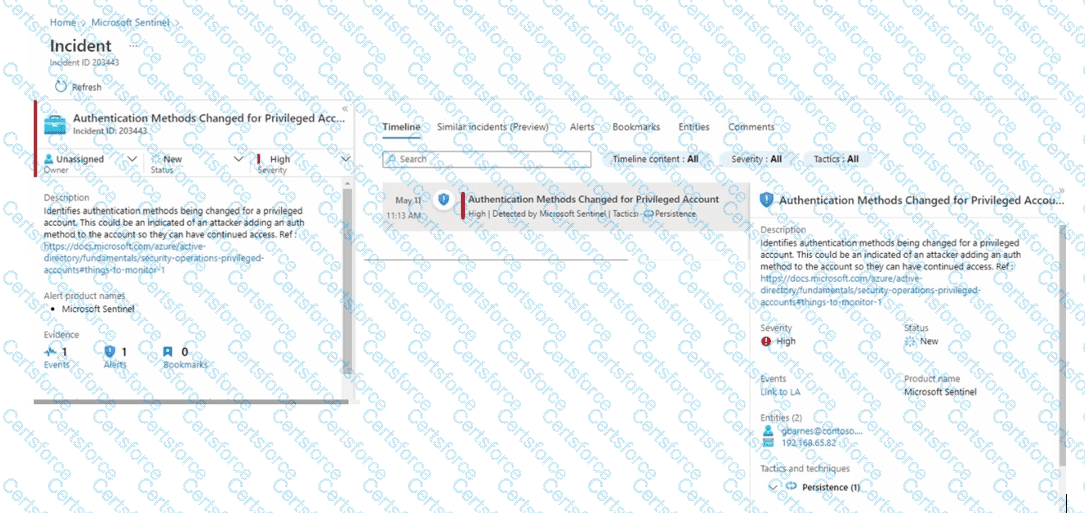
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in [the graphic.
NOTE: Each correct selection is worth one point.

You need to implement the Azure Information Protection requirements. What should you configure first?
You need to modify the anomaly detection policy settings to meet the Microsoft Defender for Cloud Apps requirements and resolve the reported problem.
Which policy should you modify?