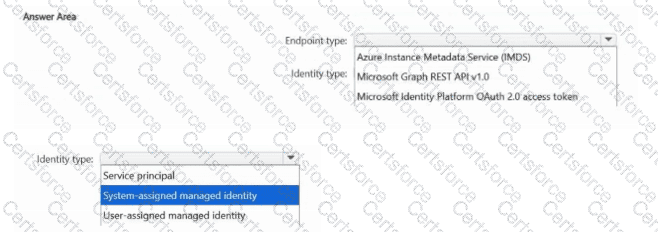
You have an Azure subscription that contains an Azure key vault named Vault1.
You plan to deploy multiple virtual machines that will host a custom app named App1. App1 will use secrets stored in Vault1. The virtual machines will be redeployed regularly based on the usage demands of App1.
You need to recommend a solution that will enable App1 to access the secrets stored in Vault1. The solution must meet the following requirements:
Minimize the number of security principals that can access Vault1.
Minimize the storage of sensitive data on the virtual machines.
Minimize administrative effort.
Which type of endpoint should App1 use to access the secrets, and which type of identity should App1 use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
A customer is deploying Docker images to 10 Azure Kubernetes Service (AKS) resources across four Azure subscriptions. You are evaluating the security posture of the customer.
You discover that the AKS resources are excluded from the secure score recommendations. You need to produce accurate recommendations and update the secure score.
Which two actions should you recommend in Microsoft Defender for Cloud? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Your company has a hybrid cloud infrastructure that contains an on-premises Active Directory Domain Services (AD DS) forest, a Microsoft B65 subscription, and an Azure subscription.
The company's on-premises network contains internal web apps that use Kerberos authentication. Currently, the web apps are accessible only from the network.
You have remote users who have personal devices that run Windows 11.
You need to recommend a solution to provide the remote users with the ability to access the web apps. The solution must meet the following requirements:
• Prevent the remote users from accessing any other resources on the network.
• Support Azure Active Directory (Azure AD) Conditional Access.
• Simplify the end-user experience.
What should you include in the recommendation?
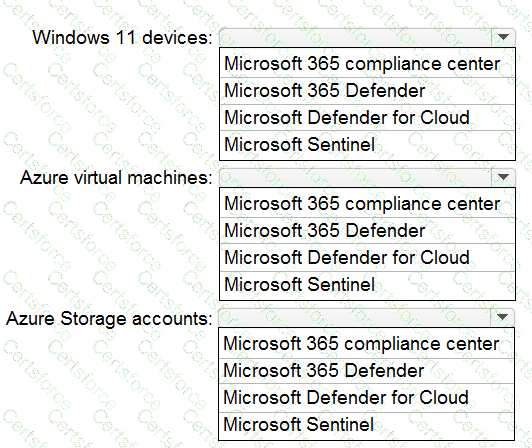
You have a Microsoft 365 E5 subscription and an Azure subscripts You need to evaluate the existing environment to increase the overall security posture for the following components:
• Windows 11 devices managed by Microsoft Intune
• Azure Storage accounts
• Azure virtual machines
What should you use to evaluate the components? To answer, select the appropriate options in the answer area.
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
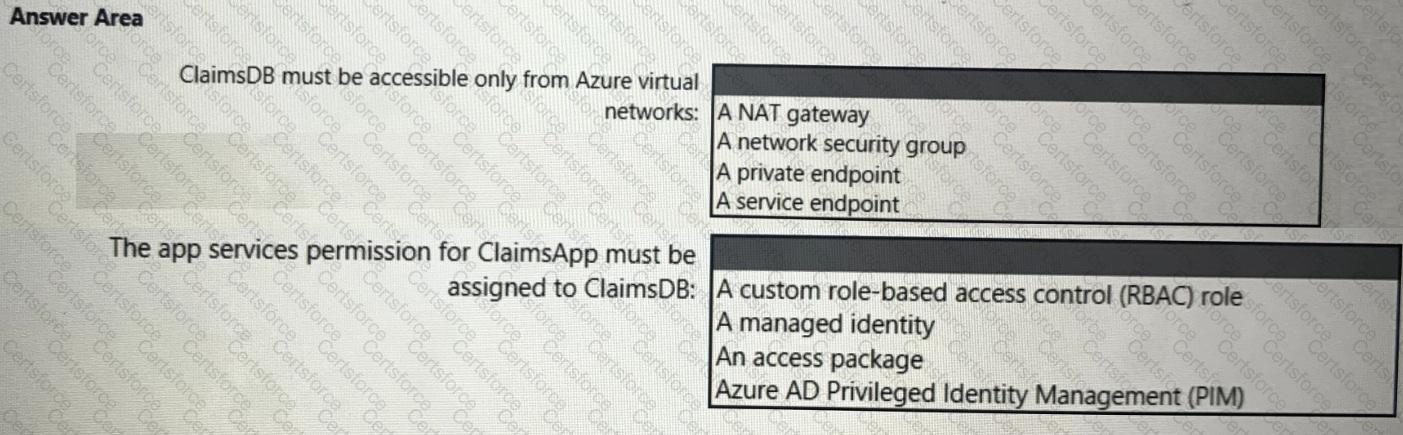
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
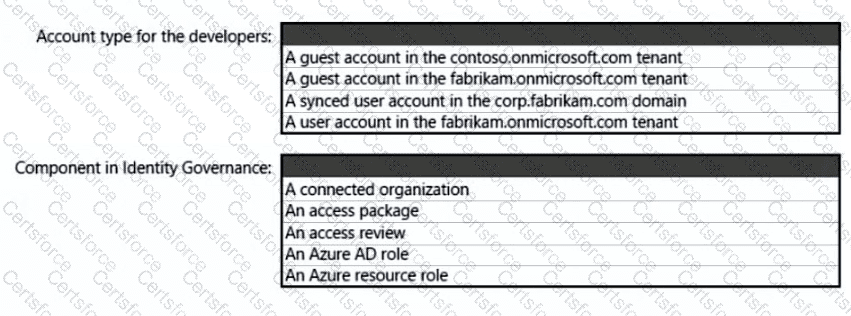
What should you create in Azure AD to meet the Contoso developer requirements?
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
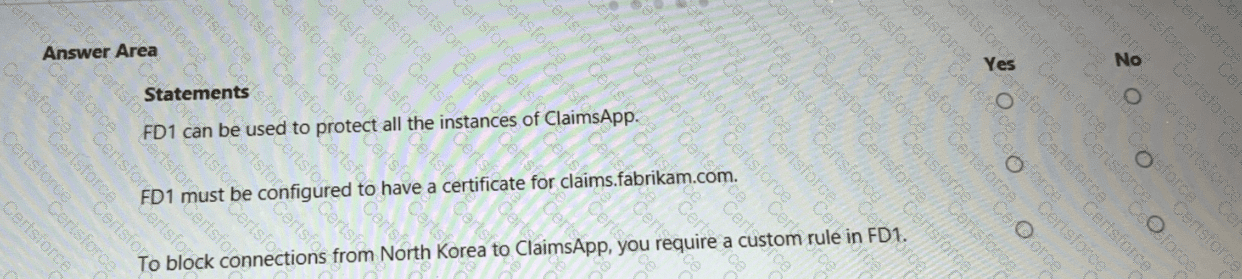
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?