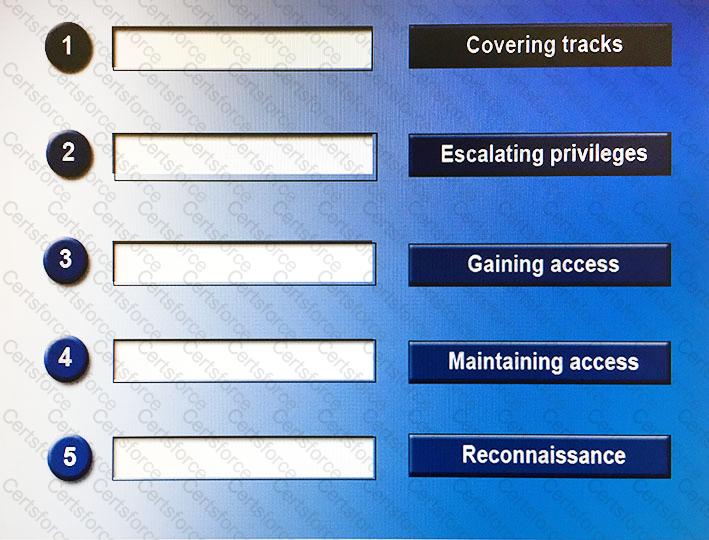
When perpetrating an attack, there are often a number of phases attackers will undertake, sometimes taking place over a long period of time. Place the following phases in the correct chronological order from first (1) to last (5).
While a network administrator is monitoring the company network, an unknown local IP address is starting to release high volumes of anonymous traffic to an unknown external IP address. Which of the following would indicate to the network administrator potential compromise?
An organization’s firewall has recently been bombarded with an excessive amount of failed requests. A security analyst has been tasked with providing metrics on any failed attempts to ports above 1000. Which of the following regular expressions will work BEST to identify an IP address with the desired port range?
From a compromised system, an attacker bypasses a proxy server and sends a large amount of data to a remote location. A security analyst is tasked with finding the conduit that was used by the attacker to bypass the proxy. Which of the following Windows tools should be used to find the conduit?
Which of the following protocols can be used for data extension?
Which of the following are legally compliant forensics applications that will detect ADS or a file with an incorrect file extension? (Choose two.)
A network administrator has been asked to configure a new network. It is the company’s policy to segregate network functions using different Virtual LANs (VLANs). On which of the following is this configuration MOST likely to occur?
An attacker performs reconnaissance on a Chief Executive Officer (CEO) using publicity available resources to gain access to the CEO’s office. The attacker was in the CEO’s office for less than five minutes, and the attack left no traces in any logs, nor was there any readily identifiable cause for the exploit. The attacker in then able to use numerous credentials belonging to the CEO to conduct a variety of further attacks. Which of the following types of exploit is described?
Which of the following commands should be used to print out ONLY the second column of items in the following file?
Source_File,txt
Alpha Whiskey
Bravo Tango
Charlie Foxtrot
Echo Oscar
Delta Roger
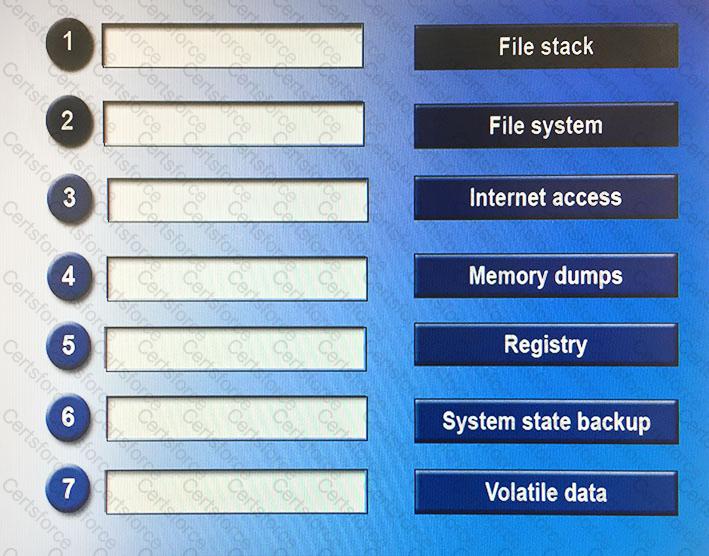
Drag and drop the following steps in the correct order from first (1) to last (7) that a forensic expert would follow based on data analysis in a Windows system.