An Aruba solution runs ArubaOS 8 and uses a mobility master architecture. Which feature can network administrators use to balance wireless devices across APs on different channels?
A network administrator wants to implement MAC filtering for the wireless network of a local financial firm to ensure that only employees can access the wireless network. What is a potential weakness of this solution?
Refer to the exhibit.
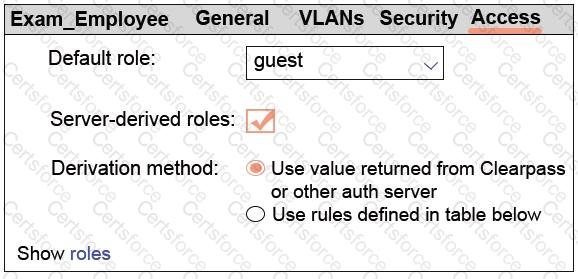
A network administrator sets up the Exam_Employees WLAN on an Aruba solution with a default role of guest, as shown in the exhibit. To which users does the guest role apply?
A customer has a large campus that requires 400 Aruba 335 APs to support a total of 20,000 wireless users and 12Gbps of traffic. Although the customer wants two controllers for redundancy, each controller must be able to support all of the APs and users on its own.
Which Aruba Mobility Controller models meet the customer requirements and DO NOT unnecessarily exceed them?
An Aruba solution has a WLAN that uses WPA2-Personal security. How are encryption keys dynamically managed for the wireless users?
A company has a single Aruba Mobility Master (MM)-based solution with two Mobility Controllers (MCs). Network administrators want APs in building 1 to support a WLAN but do not want APs in building 2 to support the WLAN.
How can administrator ensure that they can enforce this rule as they set up the WLAN in the Mobility Master (MM) Interface?
A company has a Mobility Master (MM)-based solution. A network administrator wants to monitor data transfer speed ranges of all currently connected clients.
Which dashboard page in the MM interface should the administrator visit?
A company has an Aruba solution that supports an employee WLAN. How can network administrators control in which subnets users receive IP addresses?
Which type of authentication server should administrators select to authenticate users to a ClearPass server?