John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He receives the following e-mail:
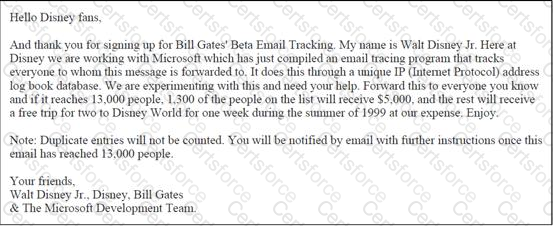
The e-mail that John has received is an example of __________.
You are the Network Administrator for a company that frequently exchanges confidential emails without outside parties (clients, vendors, etc.). You want those emails to be encrypted; however, you want the least difficulty in the encryption process. Which of the following should you choose?
The MBR of a hard disk is a collection of boot records that contain disk information such as disk architecture, cluster size, and so on. The main work of the MBR is to locate and run necessary operating system files that are required to run a hard disk. In the context of the operating system, MBR is also known as the boot loader. Which of the following viruses can infect the MBR of a hard disk?
Each correct answer represents a complete solution. Choose two.
Part of your change management plan details what should happen in the change control system for your project. Theresa, a junior project manager, asks what the configuration management activities are for scope changes. You tell her that all of the following are valid configuration management activities except for which one?
You are trying to select a particular wireless encryption algorithm. You are concerned that it implements as much of the wireless 802.11i standard as possible. Which encryption algorithm should you implement?
Which of the following techniques is based on a set of criteria that has been acquired in a specific knowledge area or product area?
Which of the following is the method of hiding data within another media type such as graphic or document?
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
John, a malicious hacker, forces a router to stop forwarding packets by flooding it with many open connections simultaneously so that all hosts behind it are effectively disabled. Which of the following attacks is John performing?
Which of the following are the countermeasures against a man-in-the-middle attack?
Each correct answer represents a complete solution. Choose all that apply.
Rick is a project manager of a construction project. He is aggregating the estimated costs of individual activities or work packages to establish a cost baseline. In which of the following Project Management Knowledge Areas is he working on?
Which of the following tools is used to hide secret data in text files and is based on the concept that spaces and tabs are generally not visible in text viewers and therefore a message can be effectively hidden without affecting the text's visual representation for the casual observer?
Which of the following types of attacks cannot be prevented by technical measures only?
You are a project manager for a recycling company. You are in the process of reviewing proposals from sellers for recycling equipment. You notice the scope statement states the company required to abide by the environmental agencies regulations regarding waste. As a result, you select proposals that automatically include features such as scrubbers and baghouses to reduce hazardous waste. Which of the following is true regarding the scope statement?
How can you calculate the Annualized Loss Expectancy (ALE) that may occur due to a threat?