Which of the following programs collects email addresses of users and creates a mailing list?
Which of the following can be performed to verify the effectiveness of a quality management system?
Which of the following is the rating for gasoline or oil fires?
During which of the following processes, probability and impact matrix is prepared?
In which of the following does a project manager assign certain points towards various categories to judge the vendors?
Which of the following is a valid space efficiency of RAID 3?
What does noise in a power line indicate?
Which of the following protocols are used to provide secure communication between a client and a server over the Internet?
Each correct answer represents a part of the solution. Choose two.
You are the Administrator of a Windows 2000 based network for Info Tech Inc. You install and configure Certificate Authorities (CAs) on the network. You are currently configuring the public key group policy for the domain.
You configure the group policy to specify automatic enrollment and renewal for certificates. But when you attempt to test this configuration, you find that the enrollment is not working properly.
What is the most likely cause?
Which of the following is a software testing method that uses an internal perspective of the system to design test cases based on the internal structure?
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 Active Directory domain-based network. The domain consists of four domain controllers, six Windows 2003 member servers, and 500 Windows XP Professional client computers. The PKI infrastructure is already configured on the network. The current configuration of the network allows only managers to use EFS on local computers. Sometimes Mark faces problems when managers lose their private keys due to the user profile becoming corrupt or being lost. Due to this, the files that were persistently encrypted by using the corresponding public key are inaccessible. He wants to restore access to the encrypted files as quickly as possible. What will he do to accomplish the task?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He writes the following snort rule:
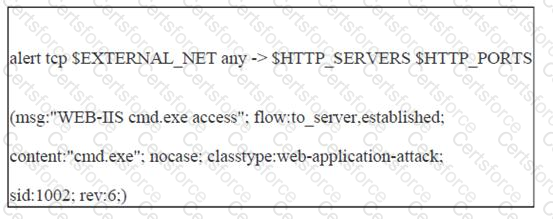
This rule can help him protect the We-are-secure server from the __________.
Which wireless security protocol is also known as IEEE 802.11i?
In Which of the following types of white box testing are the test cases designed based on data flow within the code?
Which of the following statements about Digest authentication are true?
Each correct answer represents a complete solution. Choose two.