In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)
What is the main advantage of using SD-WAN Transit Gateway Connect over traditional SD-WAN?
Refer to the exhibit
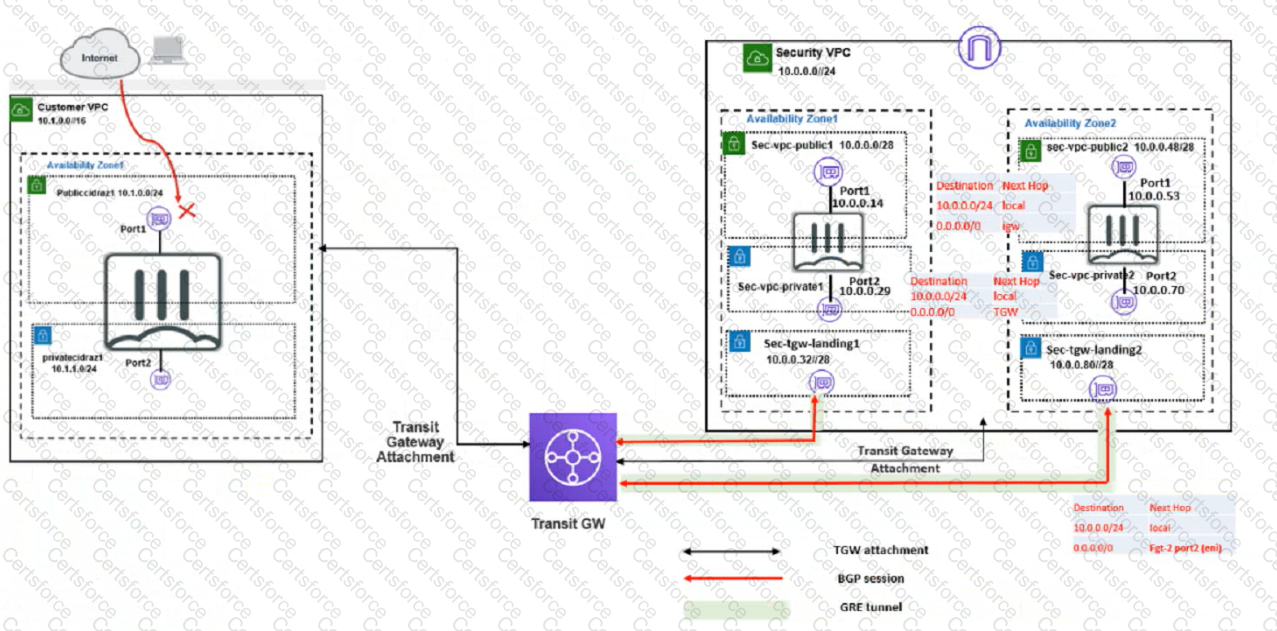
In your Amazon Web Services (AWS), you must allow inbound HTTPS access to the Customer VPC FortiGate VM from the internet However, your HTTPS connection to the FortiGate VM in the Customer VPC is not successful.
Also, you must ensure that the Customer VPC FortiGate VM sends all the outbound Internet traffic through the Security VPC How do you correct this Issue with minimal configuration changes?
(Choose three.)
Refer to the exhibit.
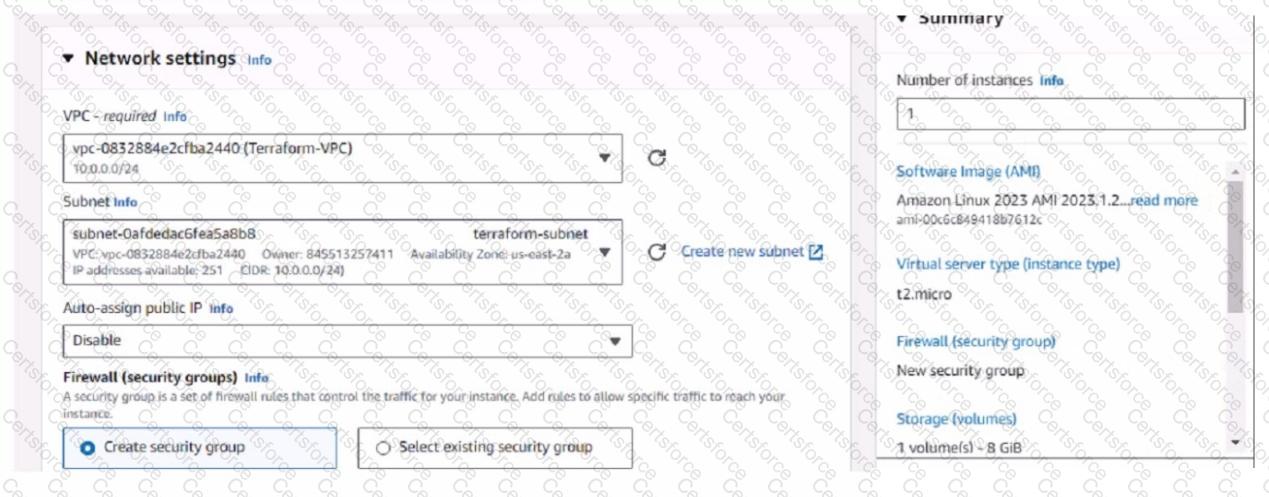
You have deployed a Linux EC2 instance in Amazon Web Services (AWS) with the settings shown on the exhibit
What next step must the administrator take to access this instance from the internet?
How does an administrator secure container environments from newly emerged security threats?
You are automating configuration changes on one of the FortiGate VMS using Linux Red Hat Ansible.
How does Linux Red Hat Ansible connect to FortiGate to make the configuration change?
An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure However, the SDN connector is failing on the connection What must the administrator do to correct this issue?
How does the immutable infrastructure strategy work in automation?
What are two main features in Amazon Web Services (AWS) network access control lists (ACLs)? (Choose two.)
Refer to the exhibit

You attempted to access the Linux1 EC2 instance directly from the internet using its public IP address in AWS.
However, your connection is not successful.
Given the network topology, what can be the issue?