What are two use cases for configuring a FortiSOAR HA cluster?
(Choose two.)
Which service on FortiSOAR is the playbook scheduler?
An administrator is issuing the following command on a node trying to join a FortiSOAR duster as a standby: csadm ha join-cluster --status active —role secondary --primary-node 10.0.1.160
The node fails to join the cluster. What is the issue?
Which two ports must be open between FortiSOAR HA nodes'* (Choose two.)
Refer to the exhibit.
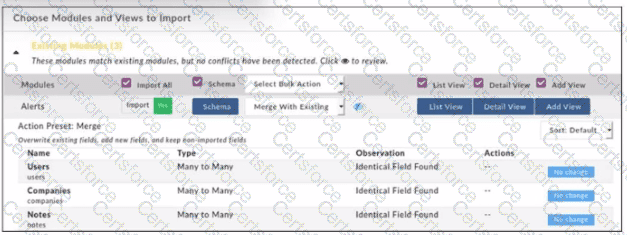
When importing modules to FortiSOAR using the configuration wizard, what actions are applied to fields it you select Merge with Existing as the Bulk action?
Which log file contains license synchronization logs on FortiSOAR?
Which SMS vendor does FortiSOAR support for two-factor authentication?
Which two relationship types are configurable on FortiSOAR?
(Choose two.)
What two permissions must you assign to a user to allow the purge of audit logs for all users? (Choose two answers)
A security analyst has reported unauthorized access to System Configuration. You must review the user's current level of access, and then restrict their access according to your organization's requirements. As part of your auditing process, which two actions should you perform? (Choose two.)