Which two purposes is the dedicated IP address used for in a FortiSASE deployment? (Choose two.)
Which two components are part of onboarding a secure web gateway (SWG) endpoint for secure internet access (SIA)? (Choose two.)
Which description of the FortiSASE inline-CASB component is true?
Refer to the exhibit.
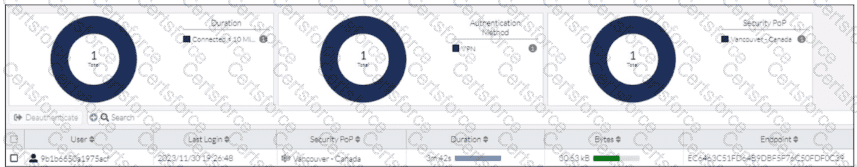
While reviewing the traffic logs, the FortiSASE administrator notices that the usernames are showing random characters.
Why are the usernames showing random characters?
A company must provide access to a web server through FortiSASE secure private access for contractors.
What is the recommended method to provide access?
What is required to enable the MSSP feature on FortiSASE?
Refer to the exhibits.
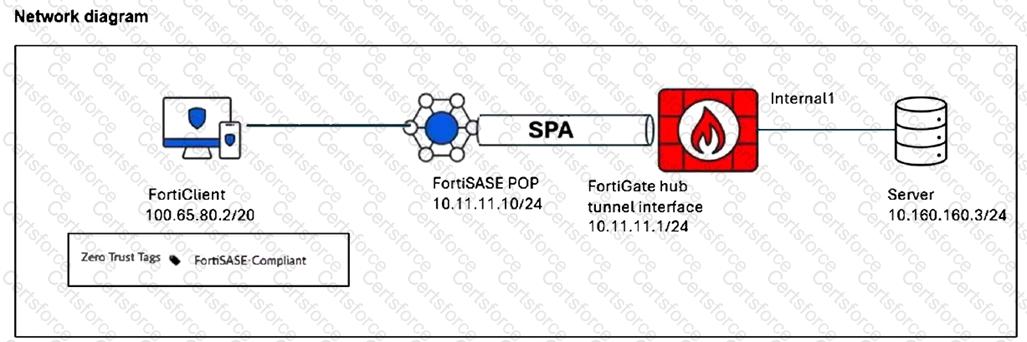
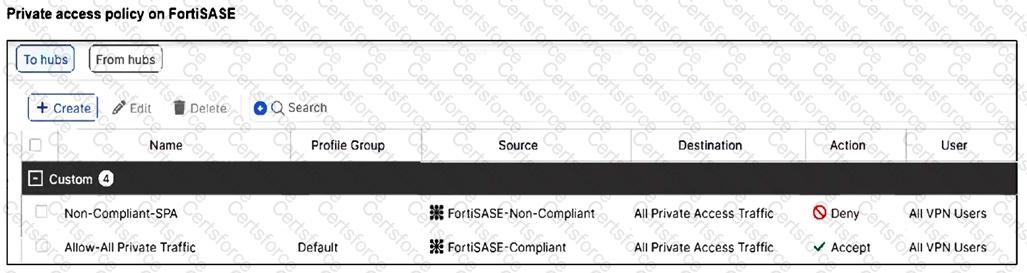
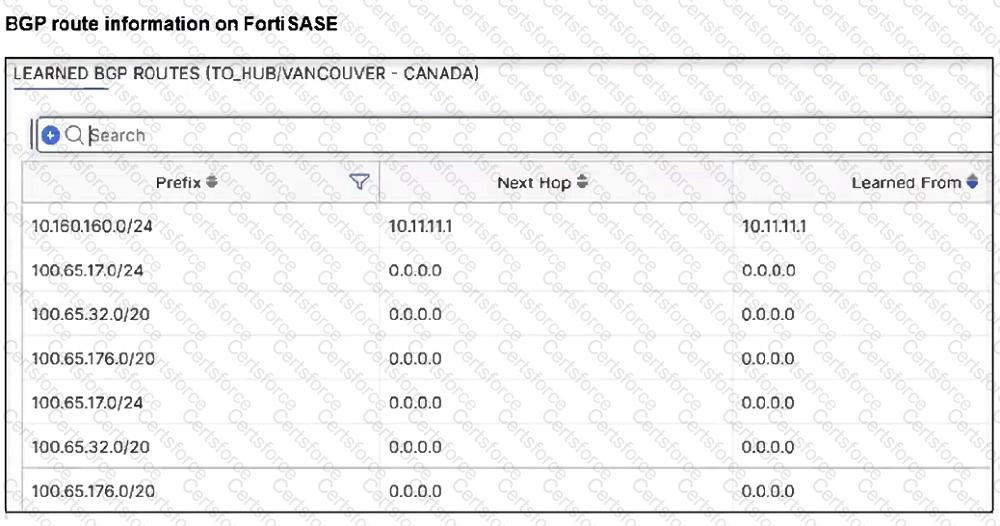
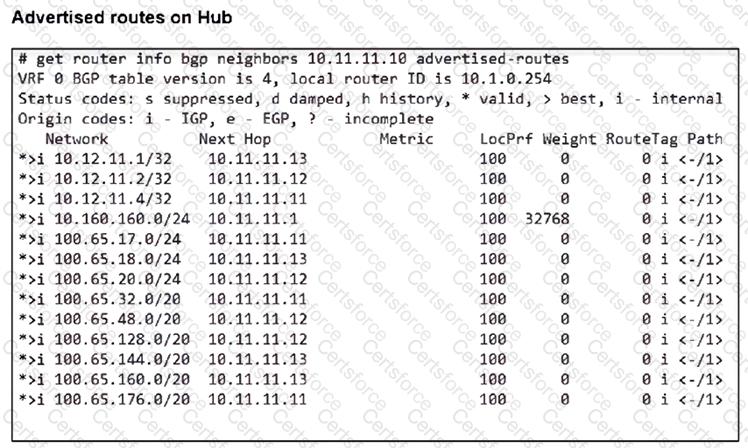
A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub.
Based on the exhibits, what is the reason for the access failure?
Refer to the exhibit.
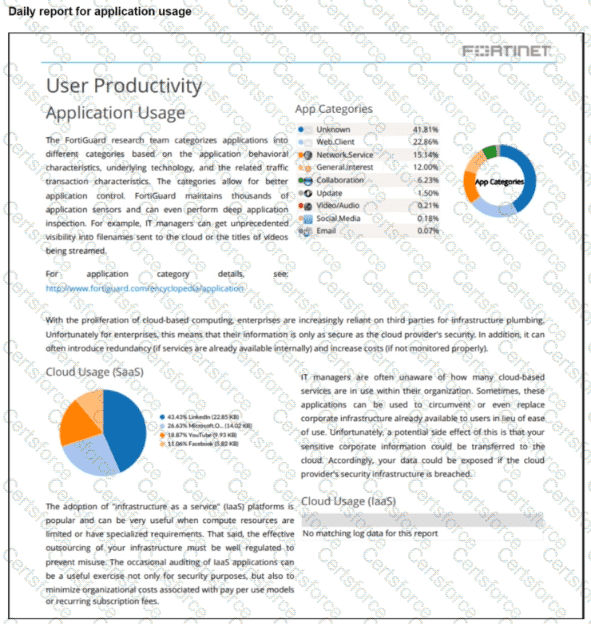
The daily report for application usage for internet traffic shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
What are two benefits of deploying FortiSASE with FortiGate ZTNA access proxy? (Choose two.)
Refer to the exhibits.
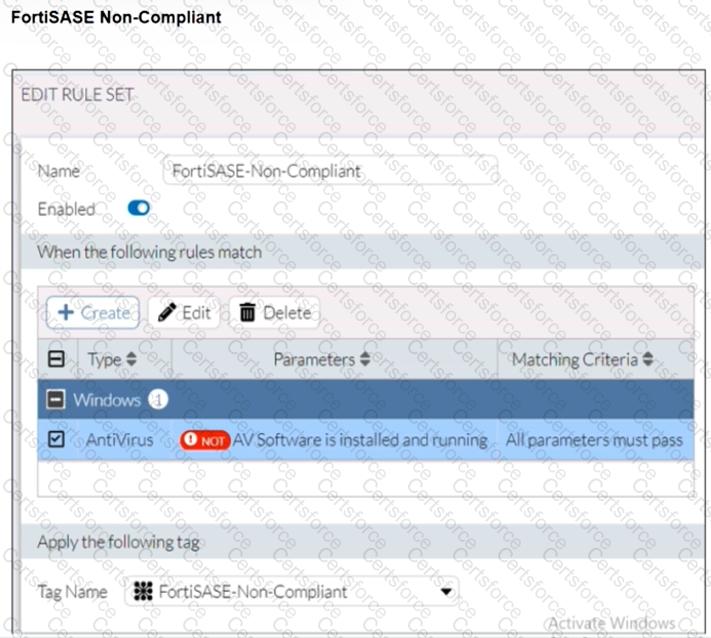
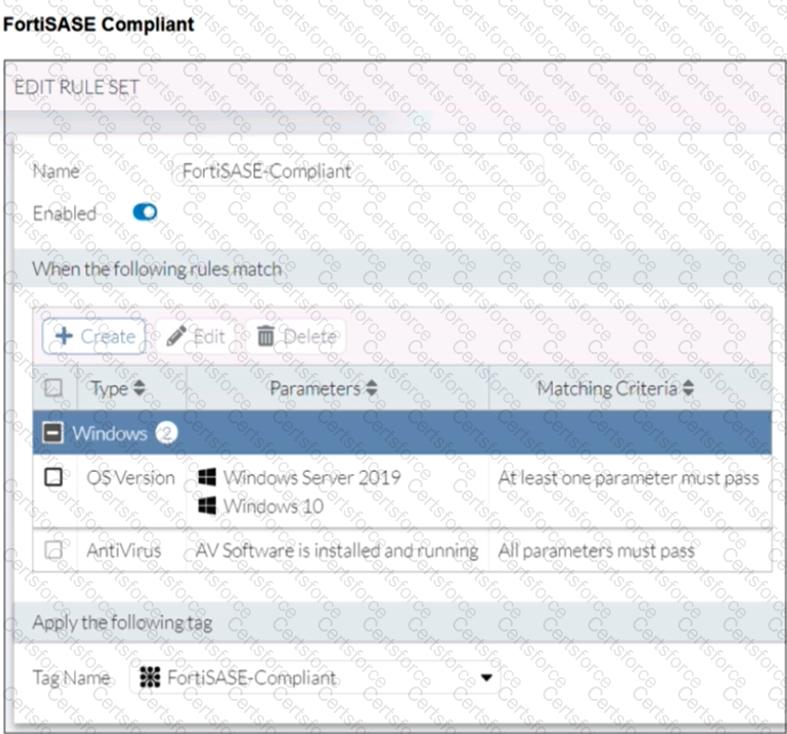
Antivirus is installed on a Windows 10 endpoint, but the windows application firewall is stopping it from running.
What will the endpoint security posture check be?