Refer to the exhibits.
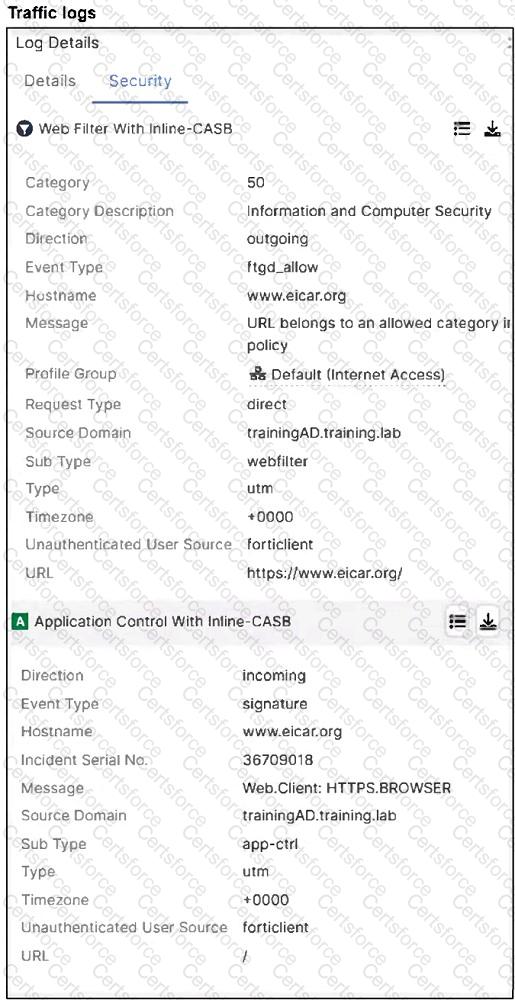
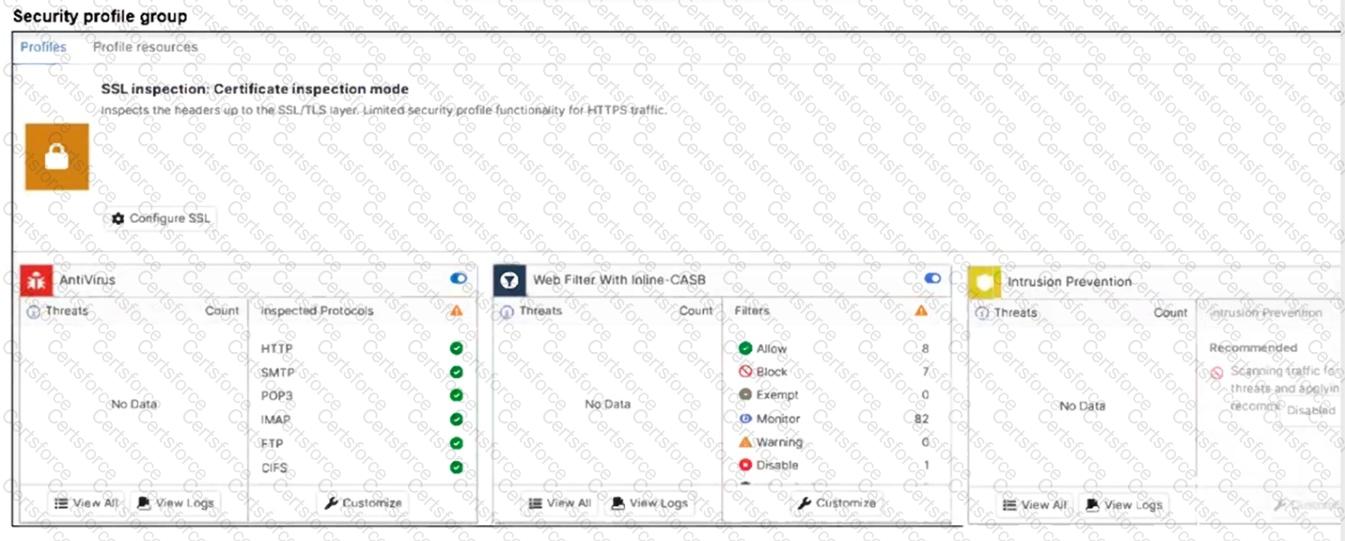
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download theeicar.com-zipfile fromhttps://eicar.org.
Which configuration on FortiSASE is allowing users to perform the download?
A- Web filter is allowing the URL.
B. Deep inspection is not enabled.
C. Application control is exempting all the browser traffic.
D. Intrusion prevention is disabled.
Refer to the exhibit.
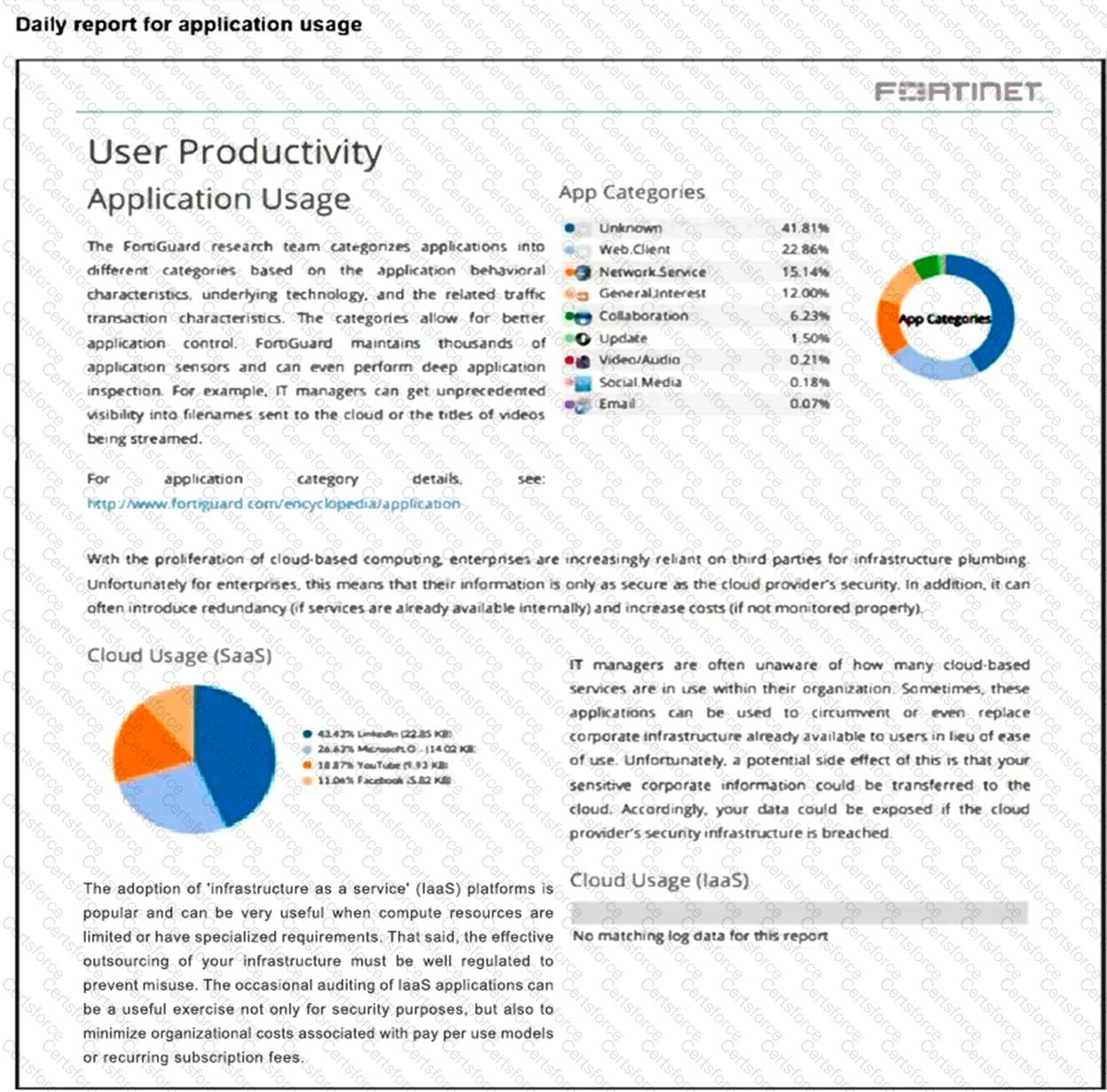
The daily report for application usage for internet traffic shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
How do security profile group objects behave when central management is enabled on FortiSASE?
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?
A company must provide access to a web server through FortiSASE secure private access for contractors.
What is the recommended method to provide access?