Refer to the exhibit.
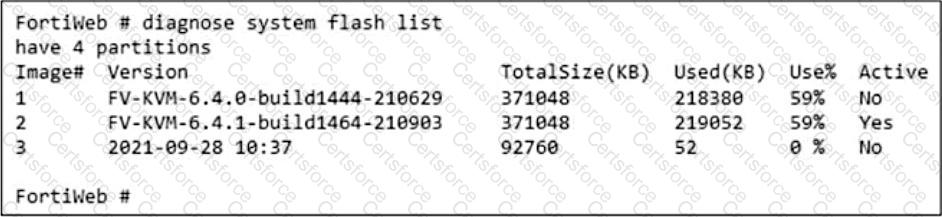
What is true about this FortiWeb device? (Choose two.)
Review the following configuration:
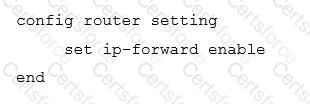
What are two routing behaviors that you can expect on FortiWeb after this configuration change? (Choose two.)
Under which two circumstances does FortiWeb use its own certificates? (Choose two.)
An administrator notices multiple IP addresses attempting to log in to an application frequently, within a short time period. They suspect attackers are attempting to guess user passwords for a secure application.
What is the best way to limit this type of attack on FortiWeb, while still allowing legitimate traffic through?
Which two functions does the first layer of the FortiWeb anomaly machine learning (ML) analysis mechanism perform? (Choose two.)
What are two possible impacts of a DoS attack on your web server? (Choose two.)
An attacker attempts to send an SQL injection attack containing the known attack string 'root'; -- through an API call.
Which FortiWeb inspection feature will be able to detect this attack the quickest?
How are bot machine learning (ML) models different from API or anomaly detection models?
Refer to the exhibit.
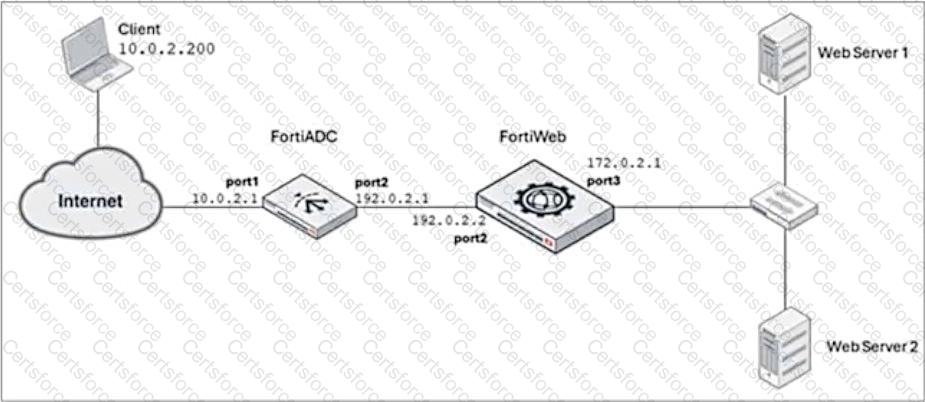
FortiADC is applying SNAT to all inbound traffic going to the servers.
When an attack occurs, FortiWeb blocks traffic based on the192.0.2.1source IP address, which belongs to FortiADC. This setup is breaking all connectivity and genuine clients are not able to access the servers.
What can the administrator do to avoid this problem? (Choose two.)
Which Layer 7 routing method does FortiWeb support?