Smith is an IT technician that has been appointed to his company's network vulnerability assessment team. He is the only IT employee on the team. The other team members include employees from
Accounting, Management, Shipping, and Marketing. Smith and the team members are having their first meeting to discuss how they will proceed. What is the first step they should do to create the network
vulnerability assessment plan?
What technique is used by JPEGs for compression?
What does Locard's Exchange Principle state?
Which of the following Windows-based tool displays who is logged onto a computer, either locally or remotely?
What is the purpose of using Obfuscator in malware?
Pick the statement which does not belong to the Rule 804. Hearsay Exceptions; Declarant Unavailable.
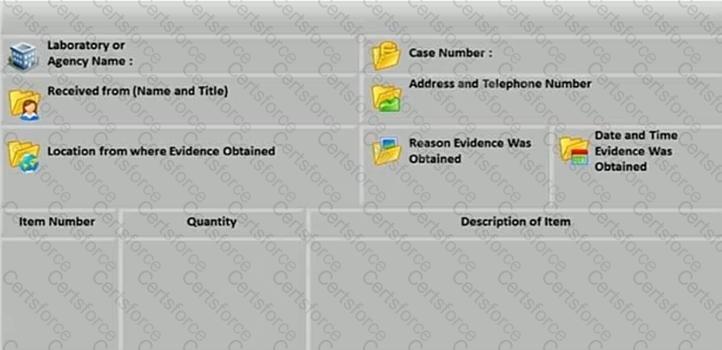
What document does the screenshot represent?
Self-Monitoring, Analysis, and Reporting Technology (SMART) is built into the hard drives to monitor and report system activity. Which of the following is included in the report generated by SMART?
Bob has encountered a system crash and has lost vital data stored on the hard drive of his Windows computer. He has no cloud storage or backup hard drives. He wants to recover all the data, which includes his personal photos, music, documents, videos, official emails, etc. Which of the following tools shall resolve Bob's purpose?
Which Event Correlation approach assumes and predicts what an attacker can do next after the attack by studying statistics and probability?
An investigator is analyzing a checkpoint firewall log and comes across symbols. What type of log is he looking at?

Chong-lee, a forensics executive, suspects that a malware is continuously making copies of files and folders on a victim system to consume the available disk space. What type of test would confirm his claim?
Which forensic investigation methodology believes that criminals commit crimes solely to benefit their criminal enterprises?
Which of these rootkit detection techniques function by comparing a snapshot of the file system, boot records, or memory with a known and trusted baseline?
Which of the following statements is TRUE with respect to the Registry settings in the user start-up folder HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\.