A small law firm located in the Midwest has possibly been breached by a computer hacker looking to obtain information on their clientele. The law firm does not have any on-site IT employees, but wants to search for evidence of the breach themselves to prevent any possible media attention. Why would this not be recommended?
In handling computer-related incidents, which IT role should be responsible for recovery, containment, and prevention to constituents?
Files stored in the Recycle Bin in its physical location are renamed as Dxy.ext, where “x” represents the ___________________.
Which of the following tool enables data acquisition and duplication?
Which program is the bootloader when Windows XP starts up?
Where are files temporarily written in Unix when printing?
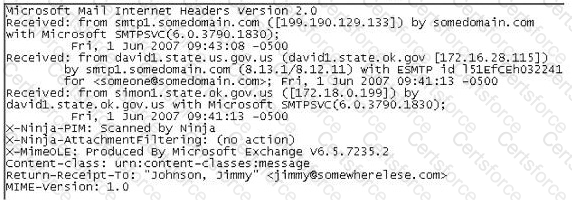
In the following email header, where did the email first originate from?
Why should you never power on a computer that you need to acquire digital evidence from?
To check for POP3 traffic using Ethereal, what port should an investigator search by?
Which network attack is described by the following statement? "At least five Russian major banks came under a continuous hacker attack, although online client services were not disrupted. The attack came from a wide-scale botnet involving at least 24,000 computers, located in 30 countries."
What type of attack sends spoofed UDP packets (instead of ping packets) with a fake source address to the IP broadcast address of a large network?
Which of the following reports are delivered under oath to a board of directors/managers/panel of the jury?
Which of the following file contains the traces of the applications installed, run, or uninstalled from a system?
Madison is on trial for allegedly breaking into her university’s internal network. The police raided her dorm room and seized all of her computer equipment. Madison’s lawyer is trying to convince the judge that the seizure was unfounded and baseless. Under which US Amendment is Madison’s lawyer trying to prove the police violated?
When is it appropriate to use computer forensics?