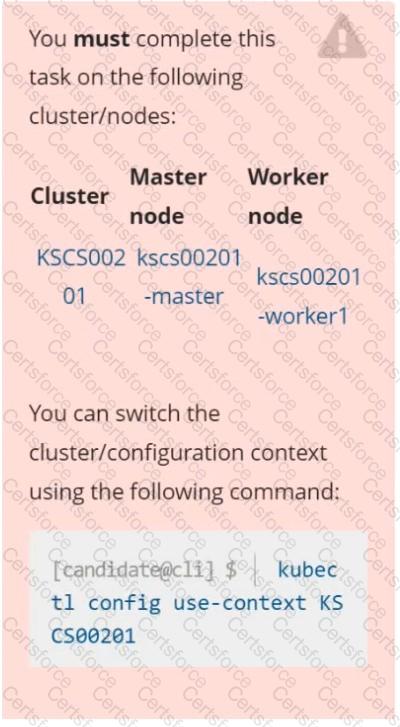
Context
A CIS Benchmark tool was run against the kubeadm-created cluster and found multiple issues that must be addressed immediately.
Task
Fix all issues via configuration and restart the affected components to ensure the new settings take effect.
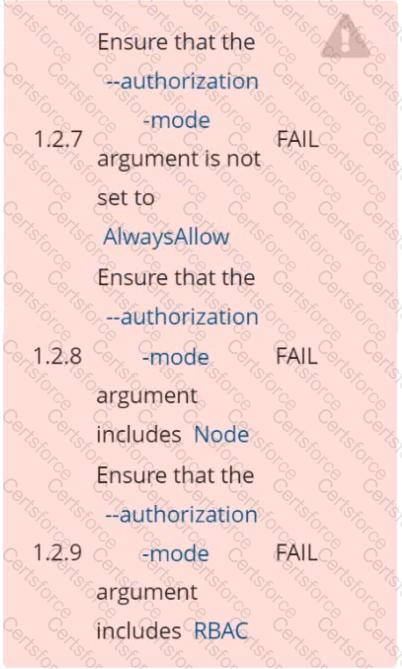
Fix all of the following violations that were found against the API server:
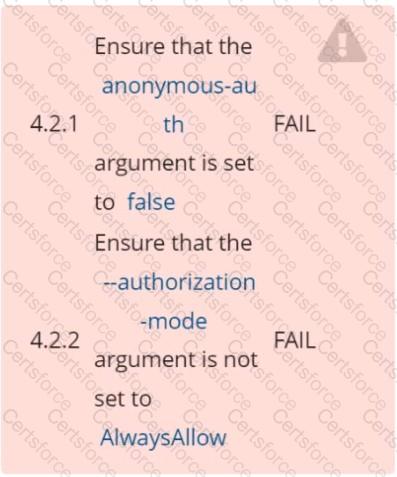
Fix all of the following violations that were found against the Kubelet:

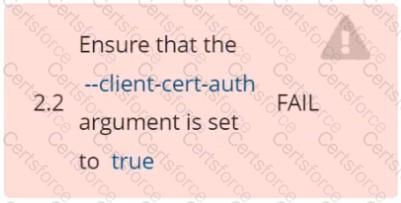
Fix all of the following violations that were found against etcd:
Submit