John works as a Network Security Professional. He is assigned a project to test the security of
www.we-are-secure.com. He establishes a connection to a target host running a Web service with netcat and sends a bad html request in order to retrieve information about the service on the host.
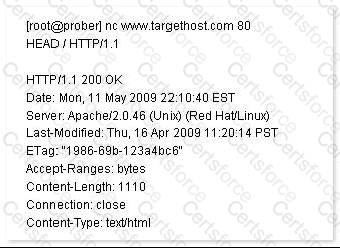
Which of the following attacks is John using?
Submit