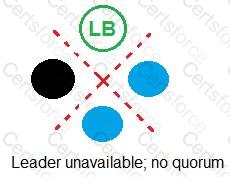
Refer to the exhibit.
In which example will auto-failover occur?

A)

B)

C)
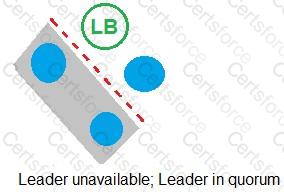
D)
You modified a Conjur host policy to change its annotations for authentication.
How should you load the policy to make those changes?
Where can all the self-signed/imported certificates be found in Conjur?
Which API endpoint can be used to discover secrets inside of Conjur?
You want to allow retrieval of a secret with the CCP. The safe and the required secrets already exist.
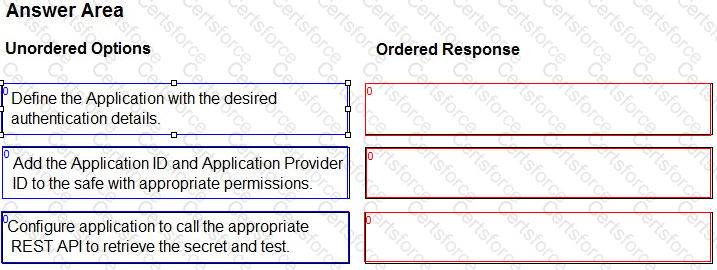
Assuming the CCP is installed, arrange the steps in the correct sequence.
You are diagnosing this log entry:
From Conjur logs:
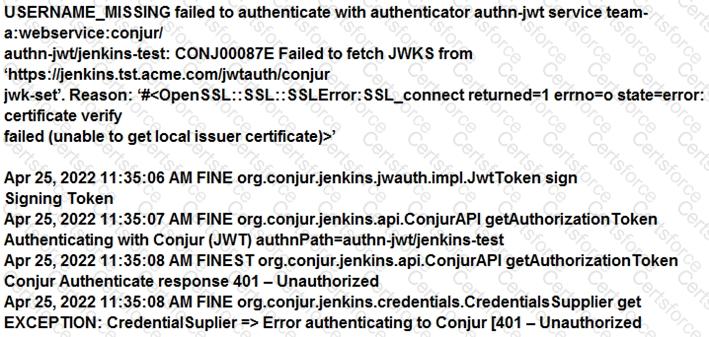
Given these errors, which problem is causing the breakdown?
When an application is retrieving a credential from Conjur, the application authenticates to Follower A. Follower B receives the next request to retrieve the credential.
What happens next?
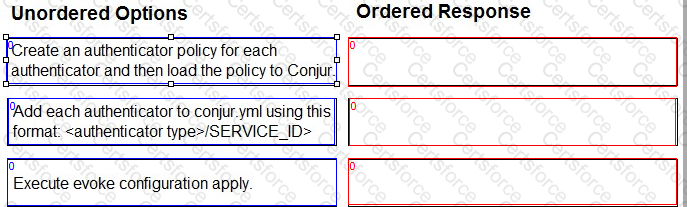
Arrange the steps to configure authenticators in the correct the sequence.
You have a PowerShell script that is being used on 1000 workstations. It requires a Windows Domain credential that is currently hard coded in the script.
What is the simplest solution to remove that credential from the Script?
What is a possible Conjur node role change?