All the desktop icons on a user's newly issued PC are very large. The user reports that the PC was working fine until a recent software patch was deployed. Which of the following would BEST resolve the issue?
A technician is an administrator on a messaging application for a private work group of mixed departments. One of the technician’s colleagues discloses to the group that their employer recently suffered a major security breach and shared details about the breach to the group Which of the following should the technician do first7
A technician thinks a customer's computer may have a malware infection and wants to determine whether the computer is in communication with any other machines. Which of the following commands should the technician use?
When a user is in the office, web pages are loading slowly on the user’s phone. Which of the following best explains this issue?
A user's corporate iPhone had issues and was repaired while the user was on vacation. The mobile phone has compared to an identical phone. Which of the following best describes what is happening to the phone?
A user reports some single sign-on errors to a help desk technician. Currently, the user is able to sign in to the company's application portal but cannot access a specific SaaS-based tool. Which of the following would the technician most likely suggest as a next step?
A user's PC is performing slowly after the user clicked on a suspicious email attachment. The technician notices that a single process is taking 100% of RAM, CPU, and network resources. Which of the following should the technician do first?
A technician is adding some Windows 10 workstations to the corporate domain. A script was able to add the majority of the workstations, but failed on a couple. Which of the following menus should the technician check in order to complete the task manually?
A web developer installs and launches a new external web server. Immediately following the launch, the performance of all traffic traversing the firewall degrades substantially. Which of the following considerations was overlooked?
A network administrator is showing an email application on a personal cell phone to a coworker. The cell phone is enrolled in the company's MDM program. When launching the application store to download the email application, the coworker receives a security warning stating the device violates company policies due to root-level access. Which of the following should the coworker perform next to resolve the issue?
A technician needs to configure a backup solution that will have the least additional expenses and impact on users. Which of the following steps should the technician complete? (Select two.)
A customer's workstation cannot connect to the internet. A technician runs a command on the workstation to view the network settings. The following is a partial readout of the response:
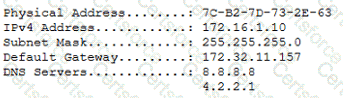
Which of the following is the most likely cause of the issue?
While testing a new computer, a technician hears a loud buzzing sound, smells smoke, and sees a flame inside the power supply. Which of the following actions should the technician take first?
A technician is performing hardware maintenance on a desktop PC. Which of the following is the most important safety precaution the technician should take?
Which of the following technologies used for wireless networks provides the greatest security?
A technician is configuring a workstation's security settings, and the following options are available:
Account lockout policy
Group policy
Two-factor authentication
Password complexity requirements
Firewalls
User accounts
Access control lists
Antivirus software
Which of the following settings should the technician configure to deploy strong password enforcement across the enterprise?
Which of the following is a preventive physical security control?
A technician is troubleshooting an issue on a PC that has low disk space. Which of the following Control Panel utilities should the technician most likely use to investigate and remediate the issue?
A technician is installing an operating system on a new computer. Which of the following is the first step of the process?
A change management review board denied an administrator's request for change. The administrator had provided the purpose and scope of the change, the date and time, and impacted systems with the risk analysis. Which of the following should be included to approve this change?