Scenario: The following NetScaler environment requirements were discussed during a design meeting between a Citrix Architect and the Workspacelab team:
All traffic should be secured, and any traffic coming into HTTP should be redirected to HTTPS.
Single Sign-on should be created for Microsoft Outlook web access (OWA).
NetScaler should recognize Uniform Resource Identifier (URI) and close the session to NetScaler when users hit the Logoff button in Microsoft Outlook web access.
Users should be able to authenticate using user principal name (UPN).
The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers and the monitor probes must be sent on SSL.
Which method can the architect use to redirect the user accessing https://mail.citrix.com to https://mail.citrix.com?
Which three tasks can a Citrix Architect select and schedule using the Citrix ADC maintenance tasks? (Choose three.)
Scenario: A Citrix Architect needs to deploy a load balancing for an application server on the NetScaler. The authentication must be performed on the NetScaler. After the authentication, the Single Sign-on with the application servers must be performed using Kerberos impersonation.
Which three authentication methods can the Architect utilize to gather the credentials from the user in this scenario? (Choose three.)
Which NetScaler Management and Analytics System (NMAS) utility can a Citrix Architect utilize to verify the configuration template created by the NMAS StyleBook, before actually executing it on the NetScaler?
Scenario: The Workspacelab team has configured their Citrix ADC Management and Analytics (Citrix Application Delivery Management) environment. A Citrix Architect needs to log on to the Citrix Application Delivery Management to check the settings.
Which two authentication methods are supported to meet this requirement? (Choose two.)
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.
Which setting is preventing the security requirements of the organization from being met?
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version 12.0.53.13 nc. After a discussion with the security team, the architect enabled the Application Firewall feature for additional protection.
In the initial deployment phase, the following security features were enabled:
IP address reputation
HTML SQL injection check
Start URL
HTML Cross-site scripting
Form-field consistency
After deployment in pre-production, the team identifies the following additional security features and changes as further requirements:
Application Firewall should retain the response of form field in its memory. When a client submits the form in the request, Application Firewall should check for inconsistencies in the request before sending it to the web server.
All the requests dropped by Application Firewall should get a pre-configured HTML error page with appropriate information.
The Application Firewall profile should be able to handle the data from the RSS feed and an ATOM-based site. Click the Exhibit button to view an excerpt of the existing configuration.
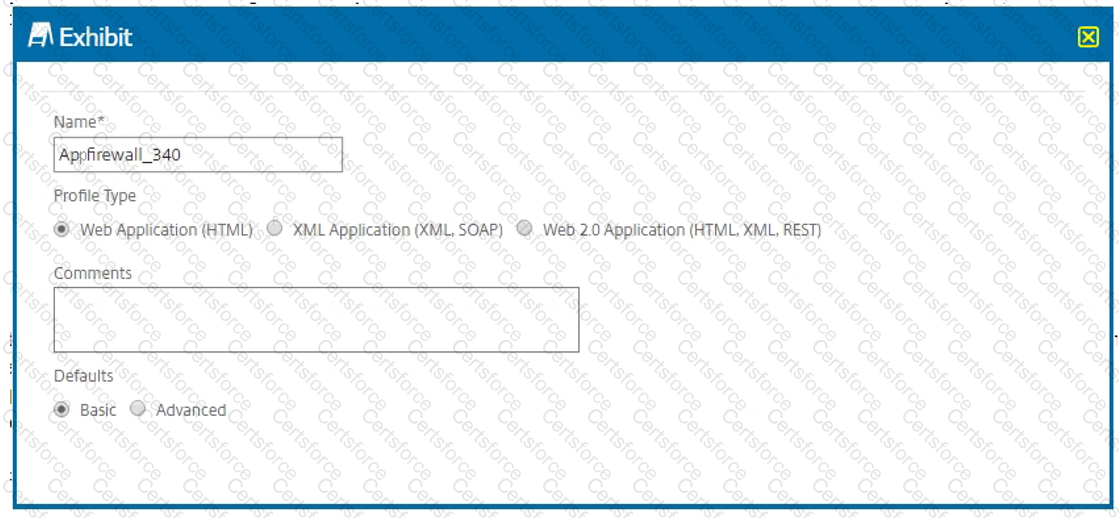
What should the architect do to meet these requirements?
Which encoding type can a Citrix Architect use to encode the StyleBook content, when importing the StyleBook configuration under source attribute?
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion. They have captured the following requirements for the Citrix ADC design project:
• The Citrix Gateway virtual server is integrated with the Citrix Virtual Apps and Desktops environment.
• The authentication must be deployed for the users from the workspacelab.com and vendorlab.com domains.
• The workspacelab users connecting from the internal (workspacelab) network should be authenticated using LDAP.
• The workspacelab users connecting from the external network should be authenticated using LDAP and RADIUS
• The vendorlab users should be authenticated using Active Directory Federation Service.
• The user credentials must NOT be shared between workspacelab and vendor) ab.
• Single Sign-on must be performed between F and Citrix Gateway.
• A domain drop down list must be provided if the user connects to the Citrix Gateway virtual server externally.
• The domain of the user connecting externally must be identified using the domain selected from the domain drop down.
At which bind point should the architect bind the domain drop-down schema policy?
Scenario: A Citrix Architect holds a design discussion with a team of Workspacelab members, and they capture the following requirements for the Citrix ADC design project:
A pair of Citrlx ADC MPX appliances will be deployed in the DMZ network and another pair in the internal network.
High availability will be accessible between the pair of Citrix ADC MPX appliances in the DMZ network.
Multi-factor authentication must be configured for the Citrix Gateway virtual server.
The Citrix Gateway virtual server is integrated with the StoreFront server.
Load balancing must be configured for the StoreFront server. •Authentication must be deployed for users from the workspacelab.com domain.
The Workspacelab users should be authenticated using Cert Policy and LDAP.
All the client certificates must be SHA 256-signed, 2048 bits, and have UserPrincipalName as the subject.
Single Sign-on must be performed between StoreFront and Citrix Gateway. After deployment the architect observes that LDAP authentication is failing.
Click the Exhibit button to review the output of aaad.debug and the configuration of the authentication policy.

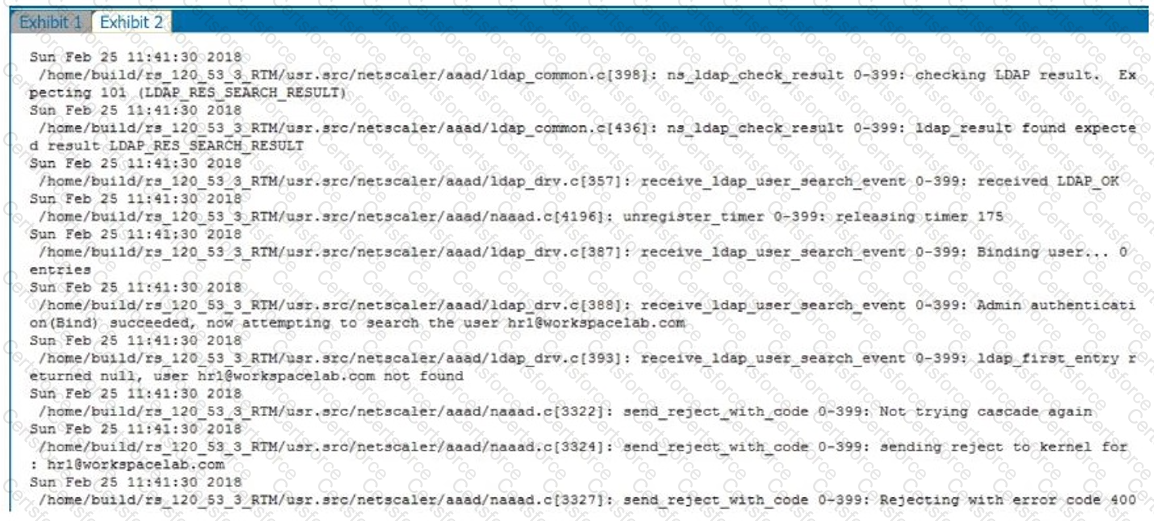
What is causing this issue?