Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.

Which setting is preventing the security requirements of the organization from being met?
For which three reasons should a Citrix Architect perform a capabilities assessment when designing and deploying a new NetScaler in an existing environment? (Choose three.)
A Citrix Architect needs to make sure that maximum concurrent AAA user sessions are limited to 4000 as a security restriction.
Which authentication setting can the architect utilize to view the current configuration?
Scenario: A Citrix Architect needs to conduct a capabilities assessment for an organization that wants to create a new Citrix ADC deployment. One of the
organization's core business drivers is to ensure that key applications are always available to users.
Which capabilities must the architect verify to assess if the requirement is feasible with the current infrastructure?
Scenario: A Citrix Architect and a team of Workspacelab members have met for a design discussion about the NetScaler Design Project. They captured the following requirements:
Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com domains.
The logon page must show the workspacelab logo.
Certificate verification must be performed to identify and extract the username.
The client certificate must have UserPrincipalName as a subject.
All the managed workstations for the workspace users must have a client identifications certificate installed on it.
The workspacelab users connecting from a managed workstation with a client certificate on it should be authenticated using LDAP.
The workspacelab users connecting from a workstation without a client certificate should be authenticated using LDAP and RADIUS.
The vendorlab users should be authenticated using Active Directory Federation Service.
The user credentials must NOT be shared between workspacelab and vendorlab.
Single Sign-on must be performed between StoreFront and NetScaler Gateway.
A domain drop down list must be provided if the user connects to the NetScaler Gateway virtual server externally.
The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.
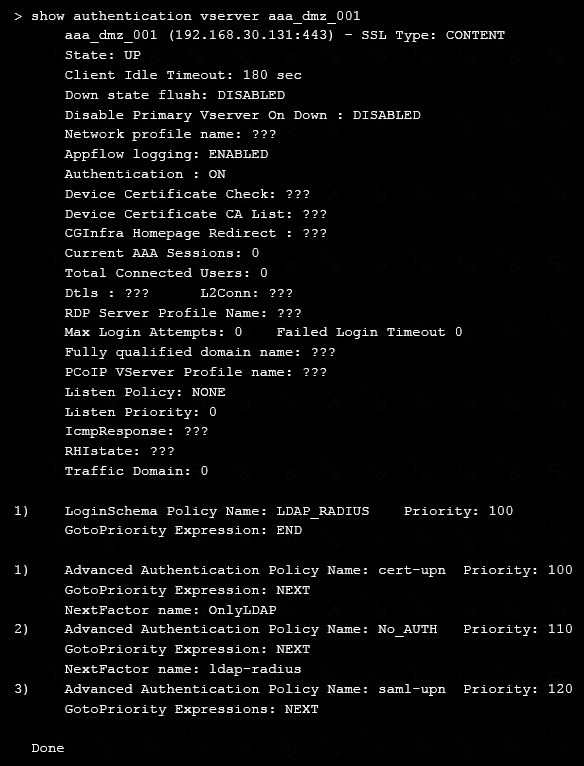
What should the architect do to correct this configuration?
A Citrix Architect needs to evaluate and define the architecture and operational processes required to implement and maintain the production environment. In which two phases of the Citrix Methodology will the architect define this? (Choose two.)
Scenario: A Citrix Architect needs to deploy Single Sign-on form-based authentication through Citrix ADC for Outlook Web Access (OWA) 2013 for the users of the domain workspacelab com The Single Sign-on (SSO) must be performed based on sAMAccountName.
Which SSO action can the architect use to meet this requirement?
Scenario: A Citrix Architect has deployed an authentication setup for the load balancing virtual server for the SAP application. The authentication is being performed using RADIUS and LDAP. RADIUS is the first factor, and LDAP is the second factor in the authentication. The Single Sign-on with SAP application should be performed using LDAP credentials. Which session profile should be used to perform the Single Sign-on?
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include Citrix Cloud as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Active Citrix Virtual App and Citrix Virtual Desktops Service subscription
No existing NetScaler deployment
Global Server Load Balancing is used to direct connection requests to Location B, if the StoreFront server in Location B fails, connections should be directed to Location A.
Click the Exhibit button to view the conceptual environment architecture.

The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)
Scenario: A junior Citrix Architect would like to use nFactor to perform authentication based on the domain. The junior architect has reached out to a supervisor for assistance and has been provided with the following step-by-step configuration guide:
Create Authentication policy for LDAP. RADIUS.
Create logon schema for Domain drop down. LDAP. LDAP+RADIUS, and noschema.
Create Authentication policy label for OnlyLDAR LDAP+RADIUS, and RADIUS.
Bind DOMAIN drop down as default logon schema policy
Create Authentication profile to bind the AAA virtual server.
Bind Authentication profile to Traffic management virtual server or Citrix Gateway virtual server.
What must the junior architect bind In order for the authentication to work correctly?