How does N5X Distributed IDS/IPS keep up to date with signatures?
Information Security Management (ISM) describes a set of controls that organizations employ to protect which properties?
Refer to the exhibit.
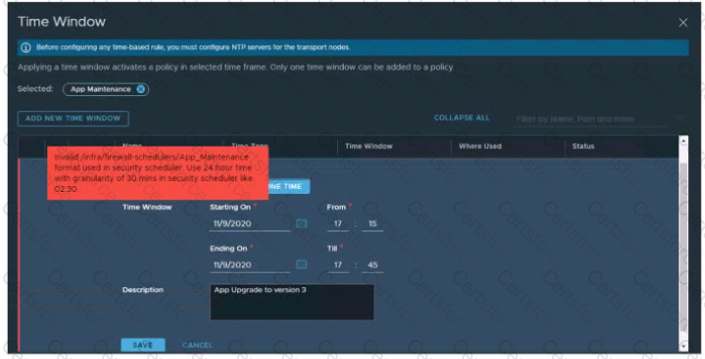
A security administrator is configuring a time window to create a time-based distributed firewall rule. While configuring the time window, an error displayed as shown in the exhibit. Which action will resolve the problem?
To which network operations does a user with the Security Engineer role have full access permission?
A security administrator is verifying why users are blocked from sports sites but are able to access gambling websites from the corporate network. What needs to be updated In nsx-T to block the gambling websites?
Which two are the insertion points for North-South service insertion? (Choose two.)
Which three criteria help to determine the severity for a Distributed IDS/IPS? (Choose three.)
What is one of the main use-cases of NSX-T Endpoint Protection?
An organization is using VMware Identity Manager (vIDM) to authenticate NSX-T Data Center users Which two selections are prerequisites before configuring the service? (Choose two.)
Which is the port number used by transport nodes to export firewall statistics to NSX Manager?