In a brownfield environment with NSX-T Data Center deployed and configured, a customer is interested in Endpoint Protection integrations. What recommendation should be provided to the customer when it comes to their existing virtual machines?
What type of IDS/IPS system deployment allows an administrator to block a known attack?
Which two statements are true about IDS/IPS signatures? (Choose two.)
Which two Guest OS drivers are required for the Identity Firewall to operate? (Choose two.)
Which of the following describes the main concept of Zero-Trust Networks for network connected devices?
An administrator wants to configure NSX-T Security Groups inside a distributed firewall rule. Which menu item would the administrator select to configure the Security Groups?
What is an unprotected traffic flow in NSX Intelligence?
Refer to the exhibit.
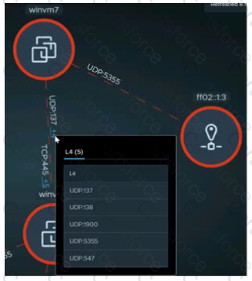
An administrator is reviewing NSX Intelligence information as shown in the exhibit.
What does the red dashed line for the UDP:137 flow represent?
An NSX administrator is trying to find the dvfilter name of the sa-web-01 virtual machine to capture the sa-web-01 VM traffic. What could be a reason the sa-web-01 VM dvfilter name is missing from the command output?
Which vCenter component is used by the NSX Manager to deploy the Partner Service VM on every host of a cluster configured for guest introspection?