When threat hunting for outliers in Splunk, which of the following SPL pipelines would filter for users with over a thousand occurrences?
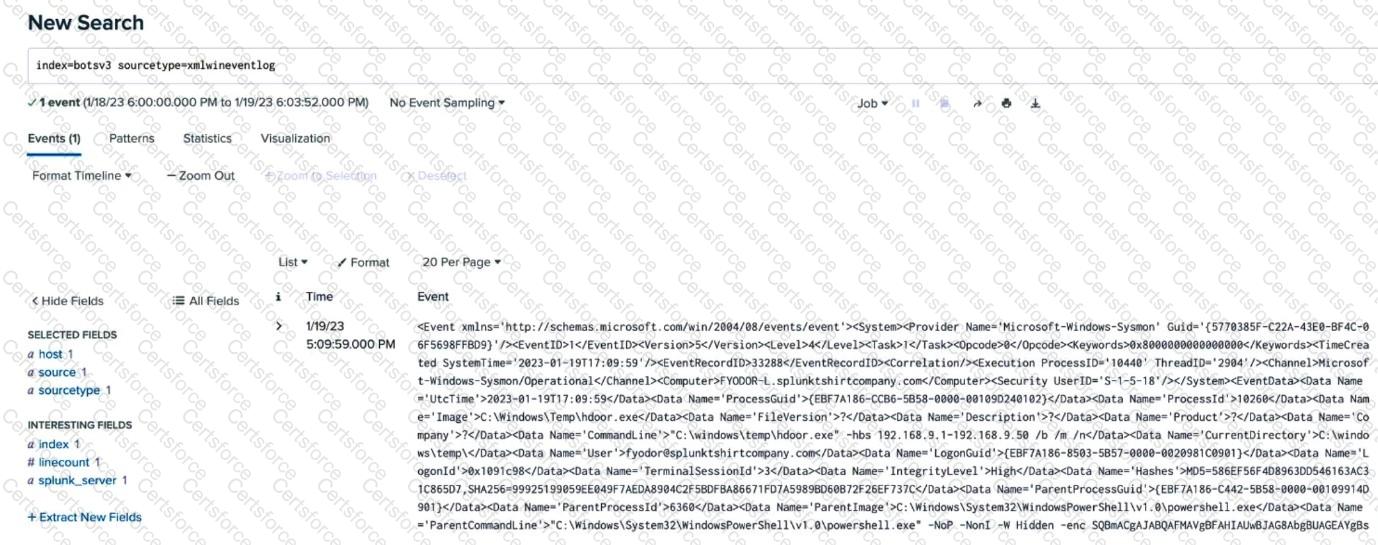
An analyst is building a search to examine Windows XML Event Logs, but the initial search is not returning any extracted fields. Based on the above image, what is themost likelycause?
An analyst would like to test how certain Splunk SPL commands work against a small set of data. What command should start the search pipeline if they wanted to create their own data instead of utilizing data contained within Splunk?
As an analyst, tracking unique users is a common occurrence. The Security Operations Center (SOC) manager requested a search with results in a table format to track the cumulative downloads by distinct IP address. Which example calculates the running total of distinct users over time?
Which of the following is not considered a type of default metadata in Splunk?
Which of the following is not a component of the Splunk Security Content library (ESCU, SSE)?
Which Enterprise Security framework provides a mechanism for running preconfigured actions within the Splunk platform or integrating with external applications?
Which dashboard in Enterprise Security would an analyst use to generate a report on users who are currently on a watchlist?
What Splunk feature would enable enriching public IP addresses with ASN and owner information?
While investigating findings in Enterprise Security, an analyst has identified a compromised device. Without leaving ES, what action could they take to run a sequence of containment activities on the compromised device that also updates the original finding?