Click the Exhibit button.
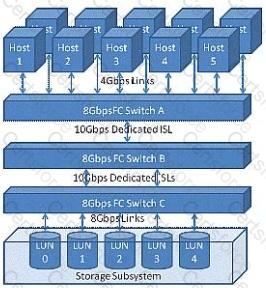
The customer application requires a 50/50 R/W ratio with 100 MBps throughput requirements for each direction of the link. The application servers will simultaneously sustain these data rates across all LUNs in parallel.
Referring to the exhibit, where will the oversubscribed link(s) occur?
A company wants to implement a database which requires a storage subsystem with no more than 2 ms write latency and 1 ms read latency.
Which type of drive would you use?
A server has lost half of its paths to its LUN on a storage system. The help desk determines that one of the two HBAs was just replaced. The SAN administrator has modified the zoning with the new WWPN of the replacement HBA port, but the missing paths have still not recovered.
Which action would you perform next?
A security audit reveals deficiencies in your company's FC zoning practices. Your manager asks you to make a recommendation to implement the most secure FC zoning possible. Your company is using switches from a single vendor.
What do you recommend?
Which storage related offering serves as intermediaries to multiple cloud storage providers?
You have been hired to consult with storage administrators that are working with zoning and naming convention consistency issues. There are numerous types of zoning methods available using standards that also include aliasing. You want to use a method that guarantees unique global port identification.
What accomplishes this goal?
Your company performs a full backup of a database server every Saturday night and incremental nightly backups for each day of the week thereafter. It takes 14 hours to perform a restore from a full backup and averages two hours for each incremental restore. The database server fails on Wednesday at 10:10 AM and needs to be fully restored.
What it is the RTO?
You have received an emergency call from the night shift after they attempted to merge three small SANs in the engineering department. Once completed, all devices in SANs A and B communicate with one another but SAN C could not communicate with either of the other SANs because the fabric has become segmented.
Which statement is correct?
You are asked to secure 2.5 PB of data so that in case of a failed drive replacement, data on the drives is not usable.
Which data protection method should be used in this case?