The Static Assembler is used to address rules assembly issues due to which cause?
Which two configurations can you use to include access groups into your Product rule? (Choose Two)
Which two statements describe the role of the cache manifest in a mobile app? (Choose two.)
Consider the following requirement: An auditing policy explicitly requires that employees cannot see the contents of complaints made against themselves.
Which security solution do you use to satisfy the requirement?
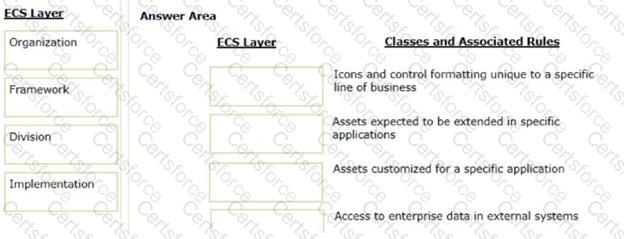
Organize the classes and associated rules in the appropriate Enterprise Class Structure (ECS) layer.
A developer has identified resource-intensive queue processors as the source of performance issues that application users are experiencing.
Which two actions do you perform to resolve the performance issues? (Choose Two)
In a hiring case type, only HR Managers should have read access to a candidate's reference letter attachment. Which two tasks are used to fulfill this requirement? (Choose Two)
A hospital uses a case type to manage the treatment of patients visiting the Emergency Room (ER). Cases are created when the patient checks in at the registration desk, and are resolved when the patient is released from the hospital. Stakeholders identify the following security requirements for the case type.
♦ Patients access cases on a read-only basis.
♦ Patients can only access their own cases.
♦ Doctors and nurses can modify cases throughout the case life cycle.
♦ Only doctors are allowed to write prescriptions.
Which configuration allows doctors and nurses to modify cases while complying with all identified security requirements?
Which two configurations do you implement when using a Pega Web Mashup? (Choose Two)
While running an application, a user notes that a system exception occurred. Which log do you review to identify the issue?