You are designing a case life cycle to process fraudulent charge claims. After a list of suspected fraudulent charge is submitted, the case advances to the processing stage. In the first step of theprocess fraud claim process, a seprate child case must be created for each suspected fraudulent charge.
After all necessary fraudulent charge cases are created, the parent cse advance to the next step where the customer is notified that their claims are being processed

choose three actions needed to configure the missing step so that a separate child case is created for
each fraudulent charge selected
What two features do activities and functions share? (Choose Two)
While configuring GetNextWork, overriding the System Settings rule
GetNextWork__WorkBasketUrgencyThreshold imposes a minimum cutoff value for assignment urgency.
Which statement accurately depicts the system behavior when the GetNextWork_WorkBaseketUrgencyThreshold setting is overridden?
You need to define a new LDAP authentication servlet because all of the standard LDAP servlets are
being used in authentication services
which two task do you perform to implement this requirement
When implementing a Next-Best-Action, the customer Lifetime value Threshold is used to __________ for an offer
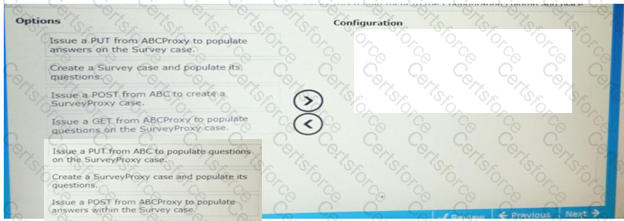
application ABC defines and creates survey cases based on a customer s profile. a second application, ABCproxy, is hosted in a cloud environment. the ABC proxy application creates a survey proxy case on demand from application ABC. The questions contained in the survey case are transferred to the survey proxy case. customers answer questions on the survey using the ABC proxy application. the completed survey information is passed back to the survey case created by application ABC. the company wants to use REST services to accomplish this interface. select and move the three options that are needed to satisfy the requirement to the configuration columns and place.
An application contains cases which transition though different statuses throughout their life cycle which typically lasts 3 months.
Design a reporting strategy to display the number of cases by status at the end of each month for a 12-month period.
A developer has set the Rule security mode on the access group to Deny. Select the reason for this setting.
Users in a cloud-based production application report a chronic performance issue that occurs every day between 2:00 P.M. and 4:00 P.M. AH attempts to reproduce the problem in the Development, QA, and Staging environments have failed.
Which two techniques help you troubleshoot the problem? (Choose Two)
APP Studio created a data type in the Organization layer for Quote data called BCO-Data Quote. How do you help users find rules from this data class when working in APP Studio?