The MyCoSelfService ruleset contains the following instances of the same rule. The only differences between the instances are the circumstance settings and ruleset version. All ruleset versions are in the ruleset list.
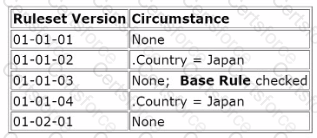
Assuming users can access all the ruleset versions, which ruleset version is chosen by rule resolution when .Country = Japan?
A Fulfillment report needs to list the user ID of the employee who packages the items to ship in an Order case. The report provides information from the MyCo-Orders-Work-Ship and Data-Admin-Operator-ID classes.
Which two options independently satisfy the report requirements? (Choose two.)
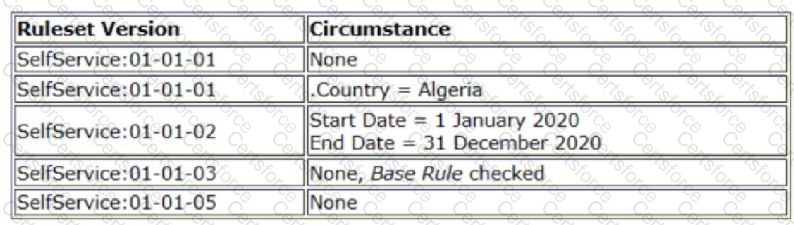
There are five instances of a rule in the rules cache. The only differences between these are the circumstance settings and ruleset version. The operator's access group has access to all ruleset versions.
On 1 June 2020, which instance is chosen by rule resolution if .Country = Algeria?
A form must support accessibility.
How do you enable a user to specify a date?
Which statement describes the appropriate use of the Purge/Archive wizard to address application performance?
You want to create a new minor version of an application ruleset to add a new feature to your application. The new feature will be made available to users in a phased rollout.
How do you update the application to add the new ruleset version?
A chemical supplier processes thousands of online orders each day. The supplier provides a material safety data sheet (MSDS) for each of the 100+ cleaning products in stock. When buyers select an item to order, the application displays the MSDS. The MSDS rarely changes.
Which of the following options ensures the MSDS is up to date when an order is created?
Drag each security solution on the left to its appropriate use case.

A flow action calls a pre-processing data transform to initiate values. There are several flow actions available for the assignment. You want to make sure that the values are only initiated once for each flow action.
How do you implement a solution?
Which three types of information can represent an attribute in attribute-based access control (ABAC)' (Choose Three)