Which two statements are valid about configuring Pega Web Mashup? (Choose Two)
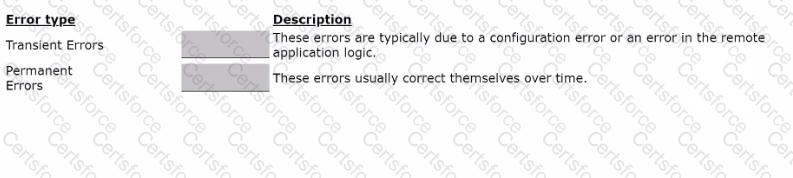
Drag the error type on the left to its description on the right.
Your application contains the following versions of a service level named AuthorizeClaim.
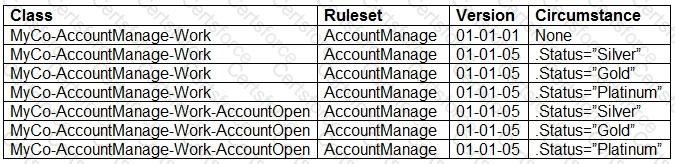
The application is being updated with a new version of the AccountManage ruleset. As part of the update, the service level is no longer circumstanced for AccountOpen cases. The update must retain the circumstancing for the other case types in the application.
Which option do you use to reset the circumstancing for the AccountOpen case type?
An assignment service-level agreement (SLA) is configured with the following details:
♦ Initial urgency: 20
♦ Assignment ready: Timed delay of 1 hour
♦ Goal: 5 hours and increase urgency by 10
♦ Deadline: 8 hours and increase urgency by 20
♦ Passed deadline: 2 hours, increase urgency by 20, and limit events to 5
Assuming no other urgency adjustments, what is the assignment urgency 16 hours after the case reaches the assignment.
Which two configurations do you implement when using a Pega Web Mashup? (Choose Two)
Place the steps in the order in which a service processes a request.

A hospital uses a case type to manage the treatment of patients visiting the Emergency Room (ER). Cases are created when the patient checks in at the registration desk, and are resolved when the patient is released from the hospital. Stakeholders identify the following security requirements for the case type.
♦ Patients access cases on a read-only basis.
♦ Patients can only access their own cases.
♦ Doctors and nurses can modify cases throughout the case life cycle.
♦ Only doctors are allowed to write prescriptions.
What two steps, when performed together, allow you to ensure that patients can read, but not edit, cases? (Choose Two)
A view has a part number field that requires the first two characters are letters, and the last four are digits (for example, AB1234).
How do you ensure that the correct pattern is entered when the user exits the field?
A developer has identified resource-intensive queue processors as the source of performance issues that application users are experiencing.
Which two actions do you perform to resolve the performance issues? (Choose Two)
Which two situations are likely to negatively impact application performance? (Choose Two)