Which two of the following are examples of audit methods that 'do' involve human interaction?
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services.
The next step in your audit plan is to verify the information security on ABC's healthcare mobile app
development, support, and lifecycle process. During the audit, you learned the organization outsourced the
mobile app development to a professional software development company with CMMI Level 5, ITSM (ISO/IEC
20000-1), BCMS (ISO 22301) and ISMS (ISO/IEC 27001) certified. The IT Manager presented the software
security management procedure and summarised the process as follows:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a
minimum. The following security functions for personal data protection shall be available:
Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and
Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report - details as follows:
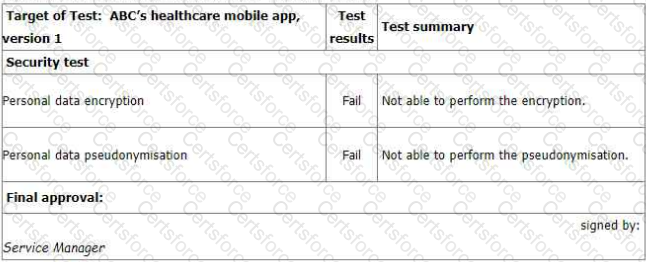
You ask the IT Manager why the organisation still uses the mobile app while personal data
encryption and pseudonymization tests failed. Also, whether the Service Manager is authorized to
approve the test.
The IT Manager explains the test results should be approved by him according to the software
security management procedure. The reason why the encryption and pseudonymization functions
failed is that these functions heavily slowed down the system and service performance. An extra
150% of resources are needed to cover this. The Service Manager agreed that access control is
good enough and acceptable. That's why the Service Manager signed the approval.
You sample one of the medical staff's mobile and found that ABC's healthcare mobile app, version
1.01 is installed. You found that version 1.01 has no test record.
The IT Manager explains that because of frequent ransomware attacks, the outsourced mobile app
development company gave a free minor update on the tested software, performed an emergency
release of the updated software, and gave a verbal guarantee that there will be no impact on any
security functions. Based on his 20 years of information security experience, there is no need to re-
test.
You are preparing the audit findings Select two options that are correct.
You are performing an ISMS initial certification audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to conduct the closing meeting. During the final audit team meeting, as an audit team leader, you agree to report 2 minor nonconformities and 1 opportunity for improvement as below:
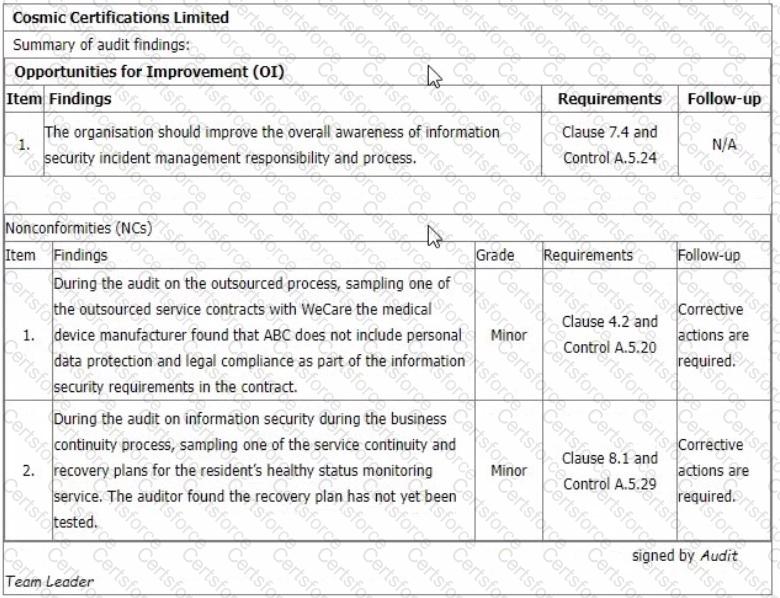
Select one option of the recommendation to the audit programme manager you are going to advise to the auditee at the closing meeting.
Scenario:
After an information security incident, an organization created a comprehensive backup procedure involving regular, automated backups of all critical data to offsite storage locations. By doing so, which principle of information security is the organization applying in this case?
Which four of the following statements about audit reports are true?
You are an experienced ISMS audit team leader guiding an auditor in training. Your team has just completed a third-party surveillance audit of a mobile telecom provider. The auditor in training asks you how you intend to prepare for the Closing meeting. Which four of the following are appropriate responses?
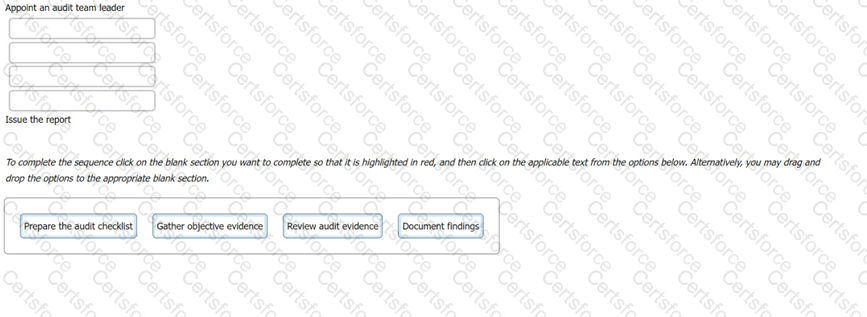
The following options are key actions involved in a first-party audit. Order the stages to show the sequence in which the actions should take place.
You are an experienced audit team leader guiding an auditor in training,
Your team is currently conducting a third-party surveillance audit of an organisation that stores data on behalf of external clients. The auditor in training has been tasked with reviewing the TECHNOLOGICAL controls listed in the Statement of Applicability (SoA) and implemented at the site.
Select four controls from the following that would you expect the auditor in training to review.
An external auditor received an offer to conduct an ISMS audit at a research development company. Before accepting it, they discussed with the internal auditor of the auditee, who was their friend, about previous audit reports. Is this acceptable?
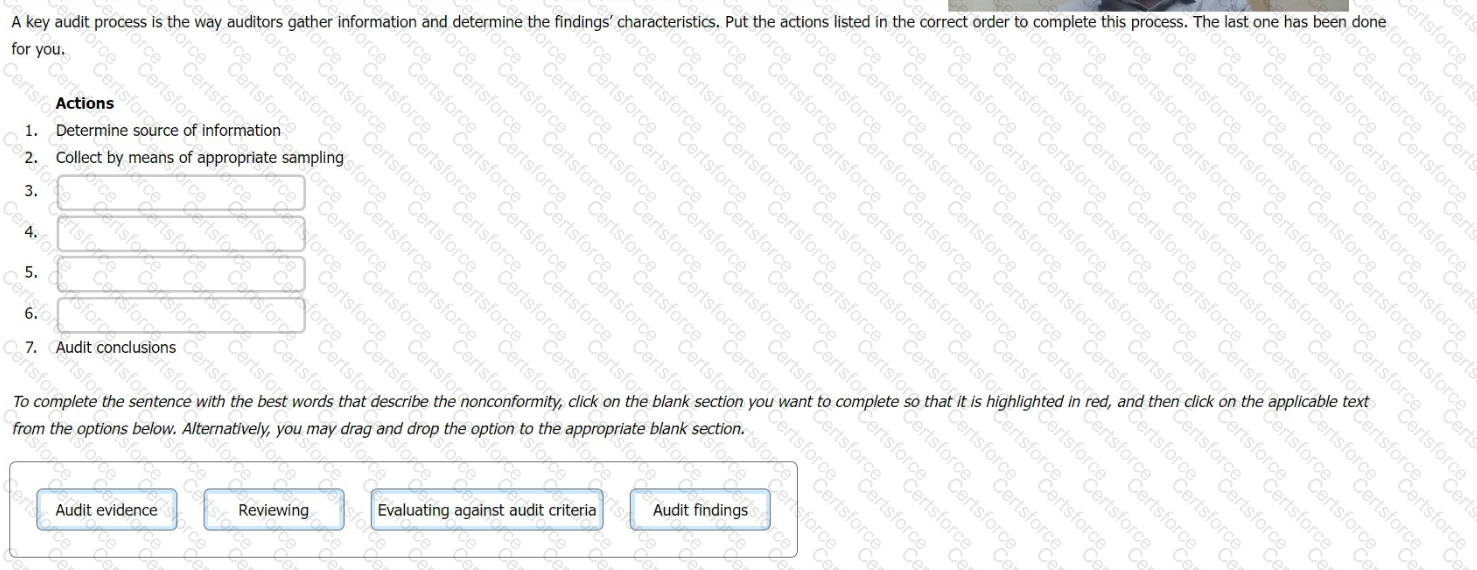
A key audit process is the way auditors gather information and determine the findings' characteristics. Put the actions listed in the correct order to complete this process. The last one has been done for you.