Palo Alto Networks recommends which two options for outbound HA design in Amazon Web Services using VM-Series NGFW? (Choose two.)
When an on-premises NGFW (customer gateway) is used to connect to the Virtual Gateway, which two IKE profiles cannot be used? (Choose two.)
Which pattern syntax will add all images to a trusted images rule within a registry?
Which statement explains the correlation between the block and alert thresholds in a vulnerability management policy?
Which RQL string using network query attributes returns all traffic destined for Internet or for Suspicious IPs that also exceeds 1GB?
Which two valid effects are used to deal with images within a rule for trusted images? (Choose two.)
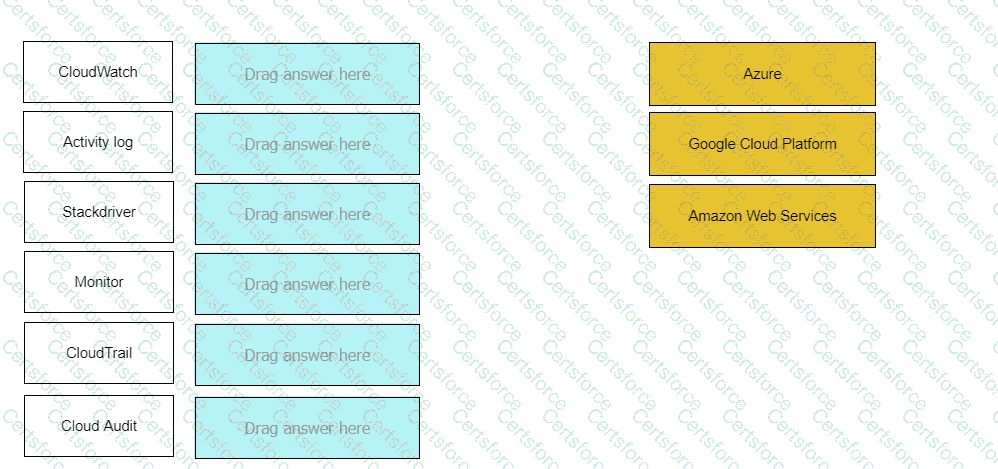
Match the logging service with its cloud provider.
Which Resource Query Language (RQL) query returns a list of all TERMINATED Google Compute Engine (GCE) instances?
Which two deployment methods are supported for Prisma Cloud Compute (PCC) container Defenders? (Choose two.)
Which pillar of the Prisma Cloud platform provides support for both public and private clouds as well as flexible agentless scanning and agent-based protection?