Which role must be assigned to DevOps users who need access to deploy Container and Host Defenders in Compute?
What is the order of steps in a Jenkins pipeline scan?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
Which alert deposition severity must be chosen to generate low and high severity alerts in the Anomaly settings when user wants to report on an unknown browser and OS, impossible time travel, or both due to account hijacking attempts?
Which options show the steps required to upgrade Console when using projects?
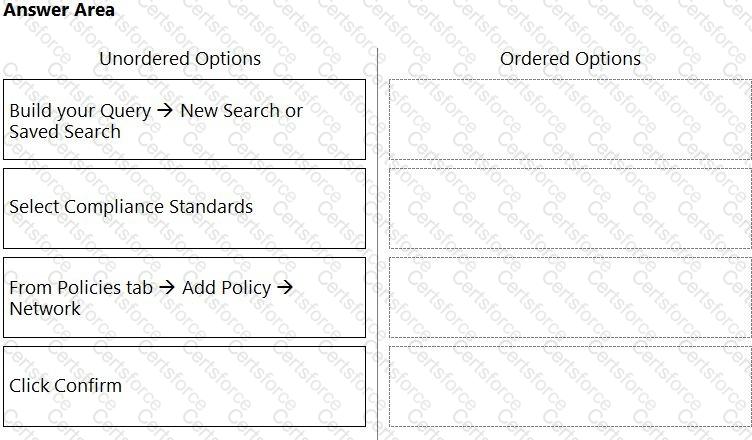
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
Which two bot types are part of Web Application and API Security (WAAS) bot protection? (Choose two.)
A customer has configured the JIT, and the user created by the process is trying to log in to the Prisma Cloud console. The user encounters the following error message:
What is the reason for the error message?
Which three elements are part of SSH Events in Host Observations? (Choose three.)