Identify a weakness of a perimeter-based network security strategy to protect an organization's endpoint systems.
Which endpoint tool or agent can enact behavior-based protection?
Which type of malware replicates itself to spread rapidly through a computer network?
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
Which characteristic of serverless computing enables developers to quickly deploy application code?
Which capability of a Zero Trust network security architecture leverages the combination of application, user, and content identification to prevent unauthorized access?
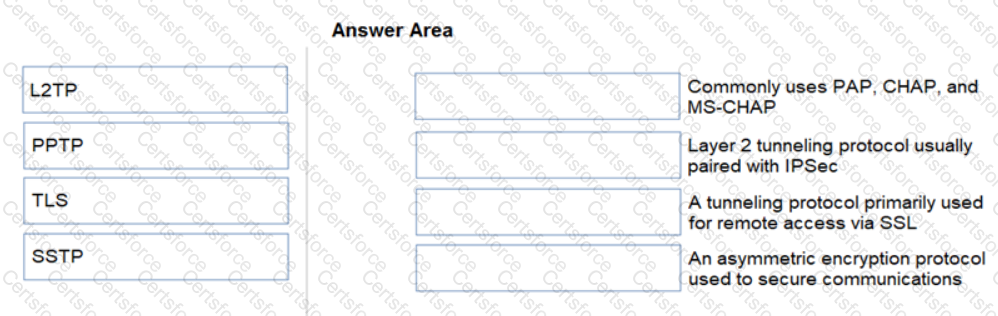
Match each tunneling protocol to its definition.
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
Which method is used to exploit vulnerabilities, services, and applications?
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?