Which IoT connectivity technology is provided by satellites?
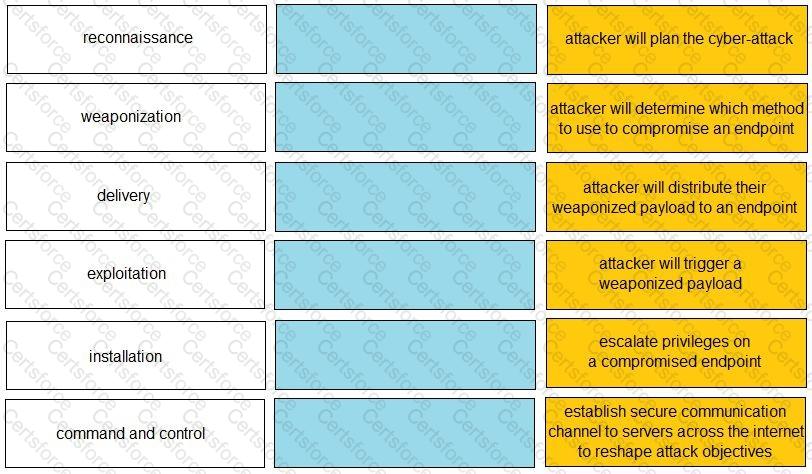
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Which three layers of the OSI model correspond to the Application Layer (L4) of the TCP/IP model?
Which protocol is used by both internet service providers (ISPs) and network service providers (NSPs)?
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
You received an email, allegedly from a bank, that asks you to click a malicious link to take action on your account.
Which type of attack is this?
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
Which network device breaks networks into separate broadcast domains?
A user is given access to a service that gives them access to cloud-hosted physical and virtual servers, storage, and networking.
Which NIST cloud service model is this?
What is a key benefit of Cortex XDR?